Legacy anti-phishing software fails to detect what we call “Microjacking” — hijacking another's Microsoft’s resources to host phishing attacks. In today's catch of the day, we share an example of this in a phishing email that INKY stopped.
Below, you'll see the potential victim receives an email containing a link to a real OneDrive or SharePoint document:
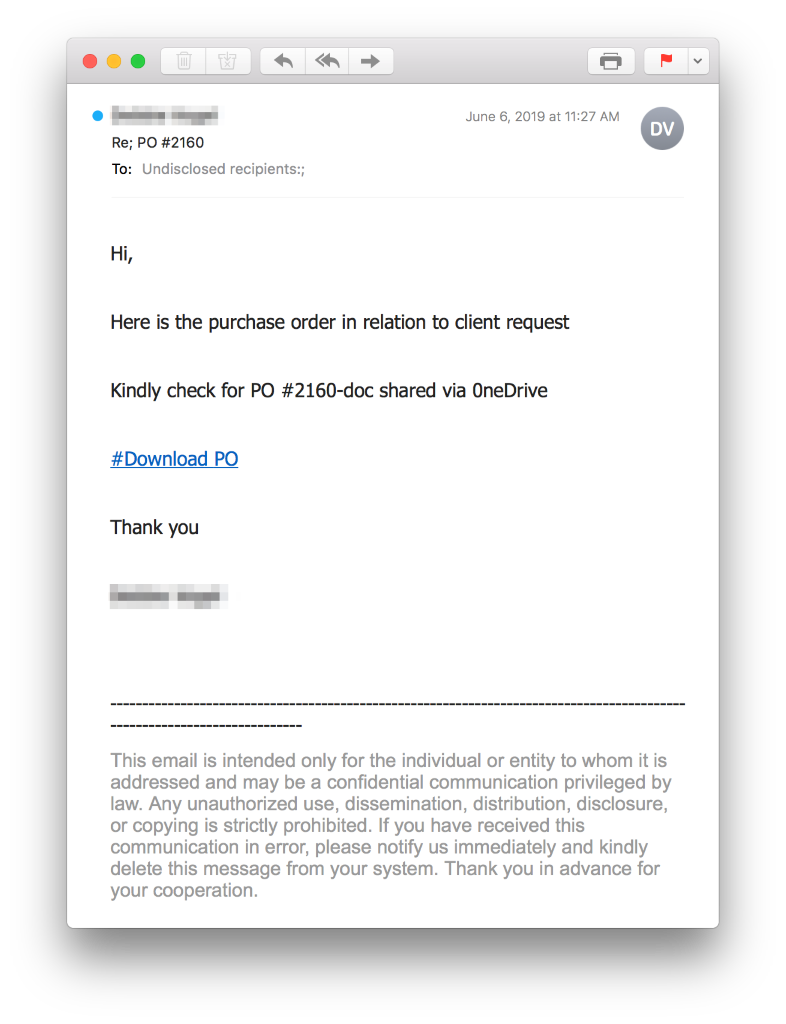
Clicking the "#Download PO" link opens the document below. This document impersonates a OneDrive request by using a hyperlink that’s actually a malicious link:
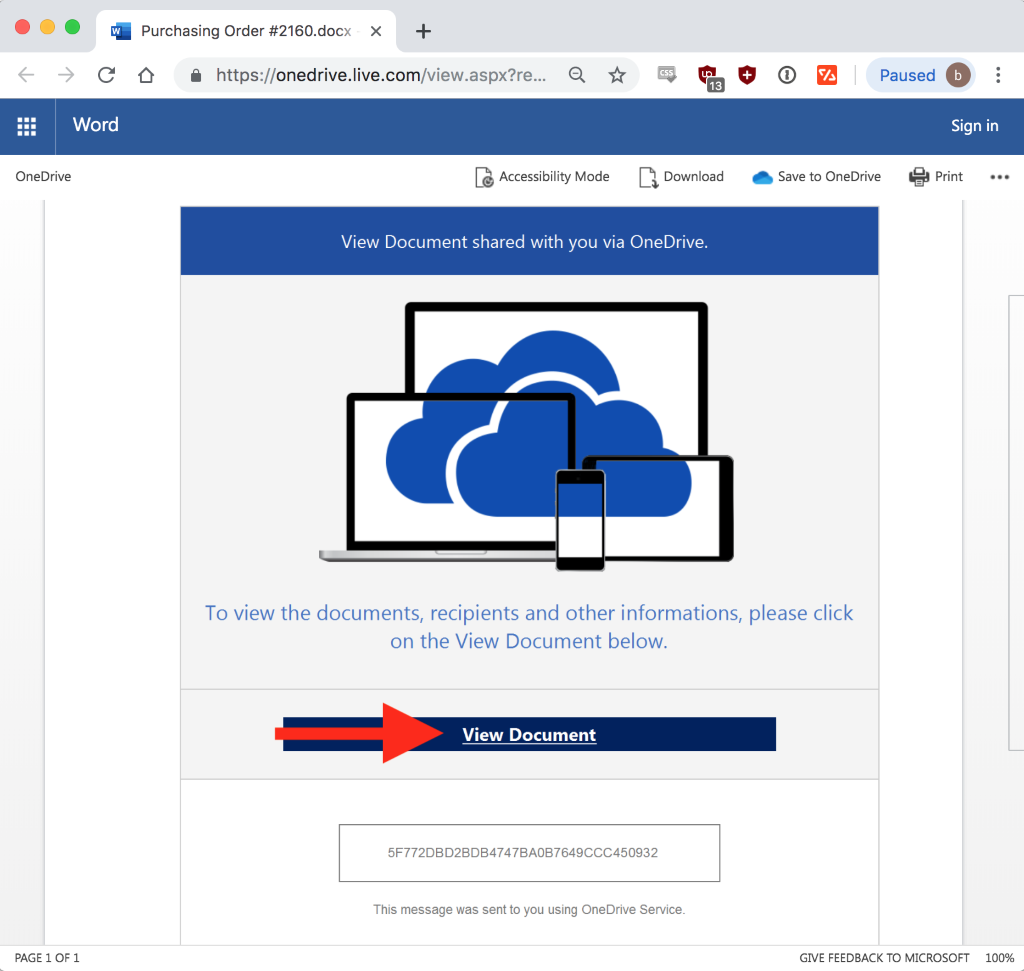
That "View Document" malicious link leads to a spoofed login used by hackers to steal login credentials:
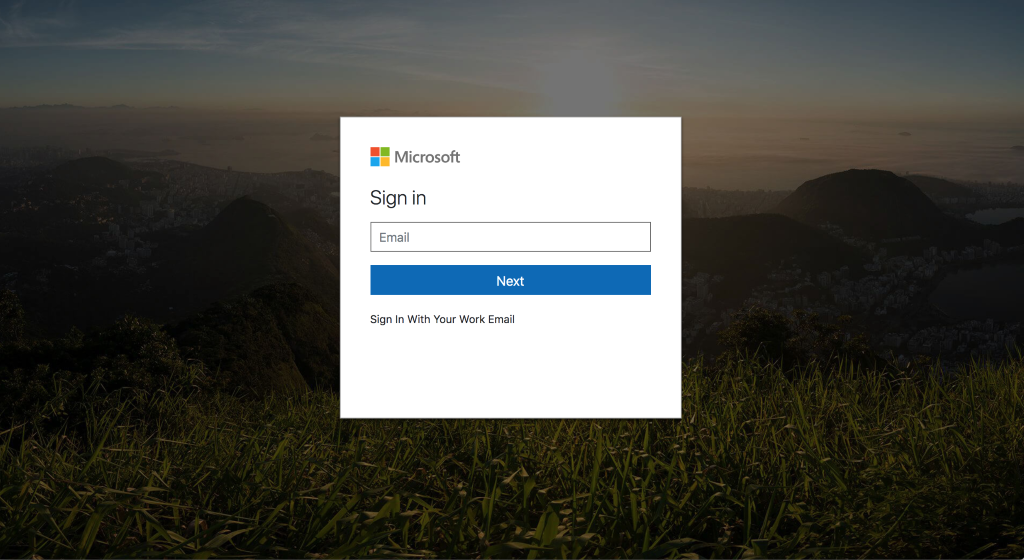
This clever trick completely bypasses anti-malware software because it’s a legitimate Microsoft link with no brand impersonation or malware to detect. Simply scanning an email for a malicious link is not enough to combat this threat. Blacklisting is futile; each document link is unique, and hackers will just create a new document with a new link.
Phishing: The Crime that Keeps on Taking
How do the hackers do it? All it takes is login credentials for one real Microsoft account to use that account to send phishing emails within and outside an organization. Hackers set up rules for incoming mail messages to be marked as read and immediately deleted after being forwarded. Usually the rules include specifics for the subject lines as well, because they will send the phishing email and then watch their own mailbox for any responses related to that message. These rule changes go unnoticed by Microjacked victim and none of these messages stay in the "Sent" folder.
How Can an Organization Protect against Microjacking?
Use INKY! INKY is proactive in monitoring and identifying new global phishing trends. This data is trained by machine learning algorithms to prevent new strains of attacks. INKY's secure email gateway will block phishing emails sent from low-reputation senders, but unlike legacy anti-phishing software, INKY uses a combination of machine learning, pattern detection, and URL structure analysis to detect Microjacking and warn users with a red "danger" banner. Schedule a demo to see for yourself.
For more email security tips and breaking news, follow INKY on LinkedIn and subscribe to this blog.


