QR Code usage has skyrocketed in recent years. In fact, 97% of consumers had no idea what a QR Code was in 2012. But by 1Q22, Americas led the world in QR code usage with 2,880,960 scans, making these quirky codes an appealing path for new and sophisticated phishing campaigns.1,2
INKY recently caught a multitude of QR Code phish, but before jumping in, we’d like to quickly make you an expert on QR Code basics. (If you’re already an expert, feel free to read ahead.)
How QR Codes Came to Be
The evolution of QR codes is pretty interesting. First came barcodes, which were developed in the 1960s in Japan when the economy was thriving. Up until that point, cashiers had to enter each price into the register by hand. Business was thriving and so was carpal tunnel syndrome. A solution was sought out and found. When scanned by an optical sensor, barcodes could quickly send the computer product and price information. The drawback was that a barcode can only hold about 20 alphanumeric characters of information. Eventually, the marketplace wanted more, and Japanese company Denso Wave Incorporated answered the call. In 1994, the first QR code was released.
The QR code’s biggest bump came in 2002 with the release of a mobile phone feature that could read the codes. Today, QR codes are considered an essential marketing tool. Sadly, it looks like QR codes are going to be pretty indispensable to phishers too.
Okay…let’s get back to our malicious QR Code phish.
Quick Response or Quickly Retrieving? What INKY Caught
Technically, QR stands for quick response because of QR codes’ ability to provide information in the snap of a finger. Unfortunately, that’s also the speed with which cybercriminals have quickly retrieving employee credentials.
INKY recently caught hundreds of QR code phishing emails and while these credential-harvesting emails came from several different hackers, the similarities are clear. They include:
- Use of image-based phishing tactic
- Microsoft impersonation
- Appearing to come from inside the recipient’s organization
- Asking the employee to resolve a particular account issue, such as 2FA setup, account verification, or password changes.
- Instilling a sense of urgency
- Repercussions for not performing the task at hand (secure your password, avoid account lockout, be held responsible)
- Prompting employees were told to scan a malicious QR code found in the email.
Let’s look at a few examples.
The example below came from a hijacked account for a Japanese retail store. INKY stopped 104 of these threats from reaching the recipients inbox.
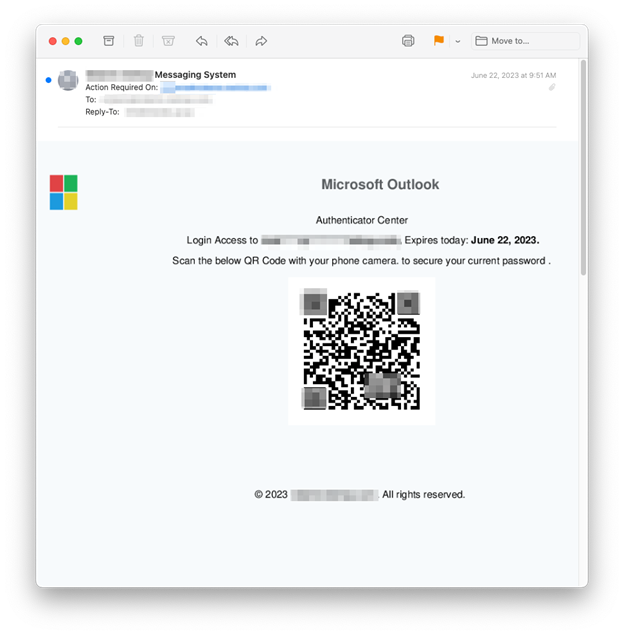
The email below is a bit different and was sent to 174 INKY users and originated from the hijacked account of an American manufacturer and several iCloud accounts that were created specifically to send phishing emails.
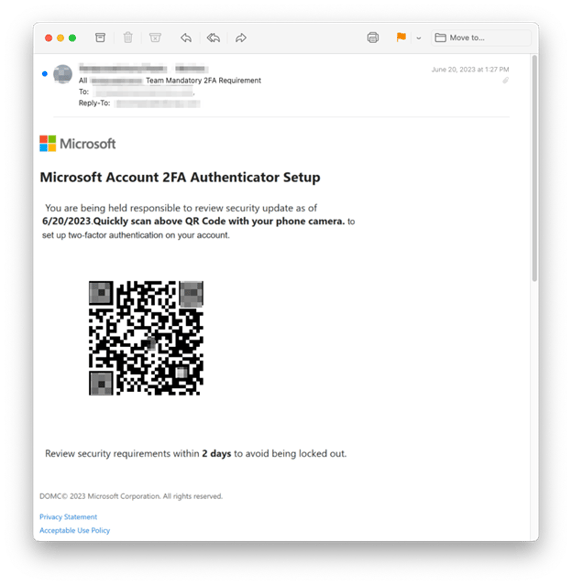
Our third example, also found below, originated from the hijacked account of a digital marketing service that operates in Canada, France, and the United States. INKY caught 267 of these destructive little phish.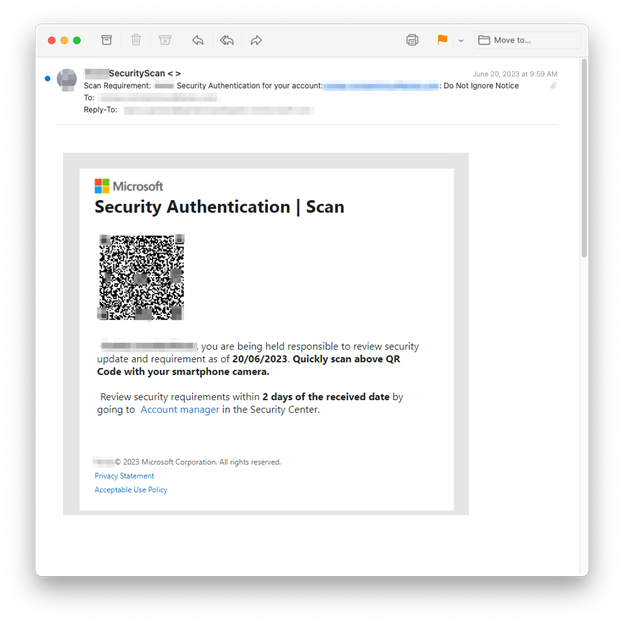
It’s important to note that these three QR Code phishing emails weren’t sent to just a handful of INKY customers. They were part of a “spray and pray” approach. Phishers send their emails to as many people as possible (spray) and then hope (pray) that a strong majority of recipients will fall for the ruse. In this case, multiple industries were attacked. Of the 545 emails noted thus far, intended victims were in the U.S. and Australia. They included non-profits, multiple wealth management firms, management consultants, a land surveyor, flooring company, and more.
The story doesn’t end here. What appears to be email text in the examples above is something altogether different.
Image-Based Phishing Messages Easily Swim by Secure Email Gateways (SEGs)
Malicious QR codes are just one part of the puzzle. Without the right email security in place, these dangerous messages would have gone undetected due to another known phishing tactic – image-based textual messages sent as an attachment.
Secure Email Gateways (SEGs) and similar security systems are designed to detect basic textual clues that signal phishing. One way around that is to design an email without text. In this case, the examples above actually contain no text. That’s right, no text. Instead, the text is embedded in an image and attached to the phishing email.
This works because most email clients automatically display the image file directly to the recipient rather than delivering a blank email with an image attached. As a result, recipients don’t know that they are looking at a screenshot of text instead of HTML code with text and since there are no links or attachments to open, the email feels safe.
Unlike SEGs, INKY uses optical character recognition (OCR) that extracts the text from an attached email and uses it in combination with other artificial intelligence algorithms to detect an email as dangerous.
Following the Malicious QR Code
INKY decoded a malicious QR code to see where it was taking recipients. As predicted, victims scanning the QR code are unknowingly taken to a phishing site so that their credentials can be stolen. Recipients are quickly made to feel comfortable because malicious links embedded in QR codes contain the recipient’s email address as a URL parameter to prefill personal data once the phishing site loads. In short, things feel familiar.
As part of the decoding, we changed the URL parameter to “batman@batman.com” and in this example, we visited hxxps://rtsp1[.]com?u=batman@batman.com
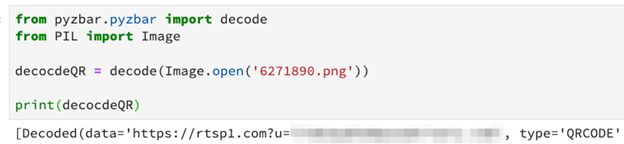
rtsp1[.]com is a newly created domain set up to redirect to y7y[.]online, another newly created domain that’s hosting a Microsoft credential harvesting site.
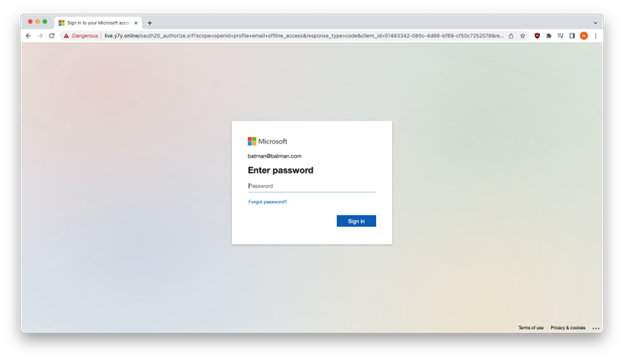
The Microsoft impersonation site accepted our fake credentials.
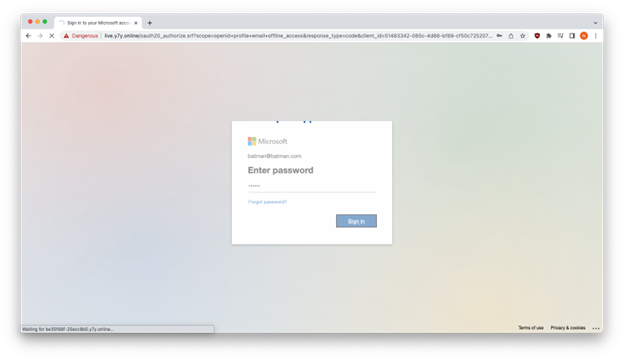
As you can see below, Google Chrome warned us that y7y[.]online harvested the fake credentials we entered.
In the end, phishers will be able to easily obtain the credentials of vulnerable, unprotected victims.
A Final Word
Let’s summarize some of the tactics used in this QR Code phishing scam.
Recap of Techniques
- Brand impersonation — uses elements of a well-known brand to make an email look as if it came from that company.
- Credential harvesting — occurs when a victim thinks they are logging in to one of their resource sites but are really entering credentials into a dialog box owned by the attackers.
- Image-based phish — textual phish message is embedded in an image.
- QR code- conceals the malicious URL from recipients and security software.
Best Practices: Guidance and Recommendations
- Recipients should use a different means of communication to confirm whenever they are requested to complete a new task.
- Carefully inspect the sender’s email address. In these cases, emails claim to come from Microsoft and the recipient’s employer but the sender’s domain has no relation to these entities.
- Don’t scan QR codes from unknown sources. Websites reached by QR codes might host malicious code that exploits vulnerabilities or steals sensitive data.
- Be cautious when entering financial and personal information on a site reached with a QR code.
INKY is the behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions regarding the safety of their email. Like a cybersecurity coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Start a free trial or schedule a demo today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.
1Source: www.inc.com/eric-v-holtzclaw/qr-codes-dont-bother-five-reasons.html
2Source: www.qrcode-tiger.com/qr-code-statistics-2022-q1
3Source: www.qrcode.com/en/history/



