Today’s phishing tale has all the makings of gangster movie – fugitives, theft, crime rings, and tax fraud. It starts with a clever phishing email that when properly unraveled, provides some added insight into the world of cybercrime. Before we get into the phish at hand (spoiler alert: tax professionals beware) we’d like to provide a little background.
FBI Brands Kim Dotcom a Fugitive and the Leader of an Internet Upload Crime Ring
As a teenager, Kim Schmitz began making illegal copies of video games, hacking into computers, and even launching a telephone scam that netted him 75,000 Deutsche Marks (worth about $41,000 today). His first arrest came at age 19 after hacking into MCI and AT&T’s PBX systems. Over the next few years, Schmitz was convicted of more than 21 charges of hacking, as well as insider trading, and internet piracy. As it turned out, he had a knack for moneymaking and cybercrime.
Schmitz legally changed his name to Kim Dotcom in 2005, that same year he founded Megaupload, a one-click hosting service where users could upload videos and large files and receive a shareable link for file downloading. It might sound legitimate enough, especially given the fact that cloud platforms like DropBox and OneDrive didn’t exist, but by early 2012, Megaupload was taken down in a global raid by the FBI. Investigators reported that the website was a hub of illegal movie and music distribution, claiming it cost copyright holders $500 million.1 Charges against Dotcom and his team included engaging in a racketeering conspiracy, conspiring to commit copyright infringement, conspiring to commit money laundering and two substantive counts of criminal copyright infringement.2
Dotcom Becomes Founder of the File Storage Service Mega
Some members of the Megaupload crew have faced legal action, but U.S. authorities are still trying to extradite Kim Dotcom from New Zealand to face charges. In 2014, shortly after his Megaupload site was seized, Kim Dotcom founded a new file storage service with a similar name, Mega. Dotcom stepped down as CEO of Mega and by 2015 had no apparent connection with the company…even though he regularly promotes MEGA on his kim.com website.
Mega is still used to store and share files online today, despite the FBI’s warnings instances where cybercriminals use Mega to upload and store stolen materials and to infect unknowing visitors with malware.3
INKY’s Interesting Mega Phish
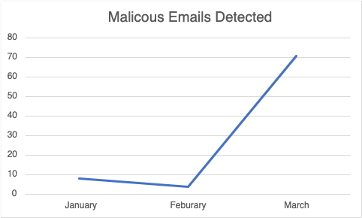
Catching phish can be taxing – especially leading up to April 15th. This year, INKY detected a phishing campaign targeting tax professionals which began in January and increased significantly in March.
According to the IRS, tax professionals are regularly targeted this time of year as hackers devise schemes to steal data, impersonate clients, and file fraudulent tax returns.
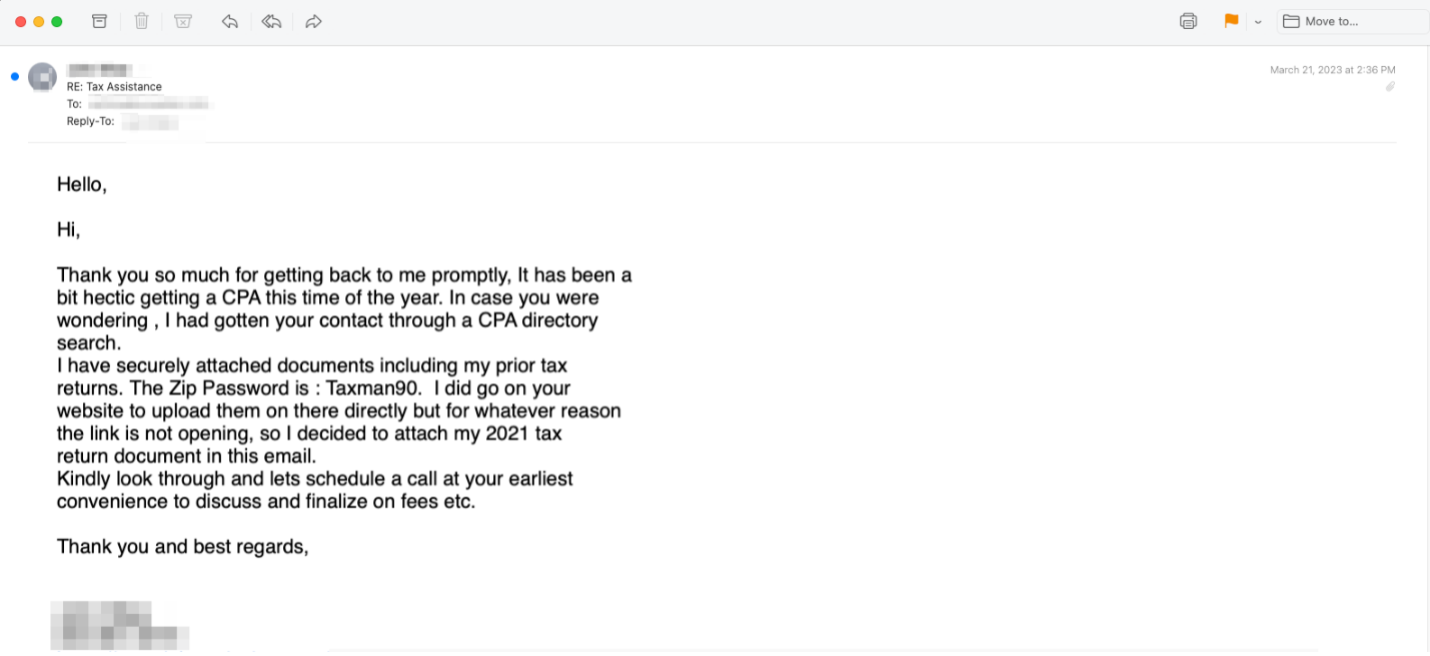
In this phishing scam, tax professionals were recipients of an email claiming that the sender found their contact information while searching for a CPA (Certified Public Accountant). Along with the email, the sender mentions that their prior tax return is attached.
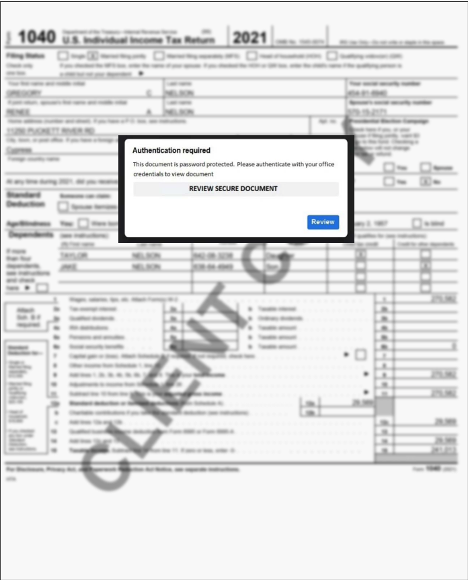
What the tax professional sees next is a blurry 2021 1040 tax return in the form of a PDF that appears to be a secured document.
What victims are not aware of is that a link to mega[.]nz (MEGA) has been added to the image in the PDF attachment they are about to view.
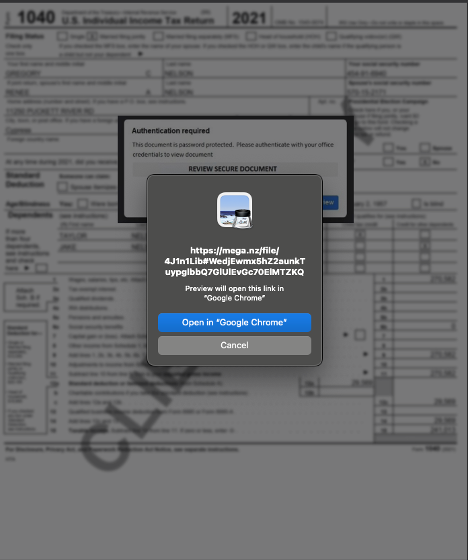
As you can see above, the hacker is using the file storage service, Mega. Clicking on the link brings recipients to a password protected zip file hosted on Mega.
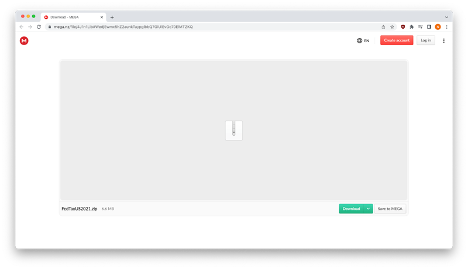
From there, should the reader choose to continue, a zip file will download and decompress, ultimately revealing a video and malicious LNK file named “FedTaxUS.pdf.lnk”
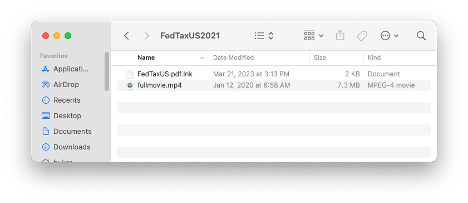
LNK is a file format used by Windows OS as a shortcut to act as a pointer to open a file, folder, or application. LNK files are based on Shell Link binary file format (file-based shortcuts) which holds information used to access another data object. This means that this file type can maliciously execute anything on a victim’s computer. Phishers are looking for innovative ways to avoid detection after Microsoft started to automatically disable macros in email attachments and LNK files provide a new way for attackers to gain access to systems for downloading and executing malicious payloads.
Uploading the LNK file to VirusTotal reveals that it’s used to download and execute Remcos remote access trojan to fully control the victim’s computer and collect sensitive information.
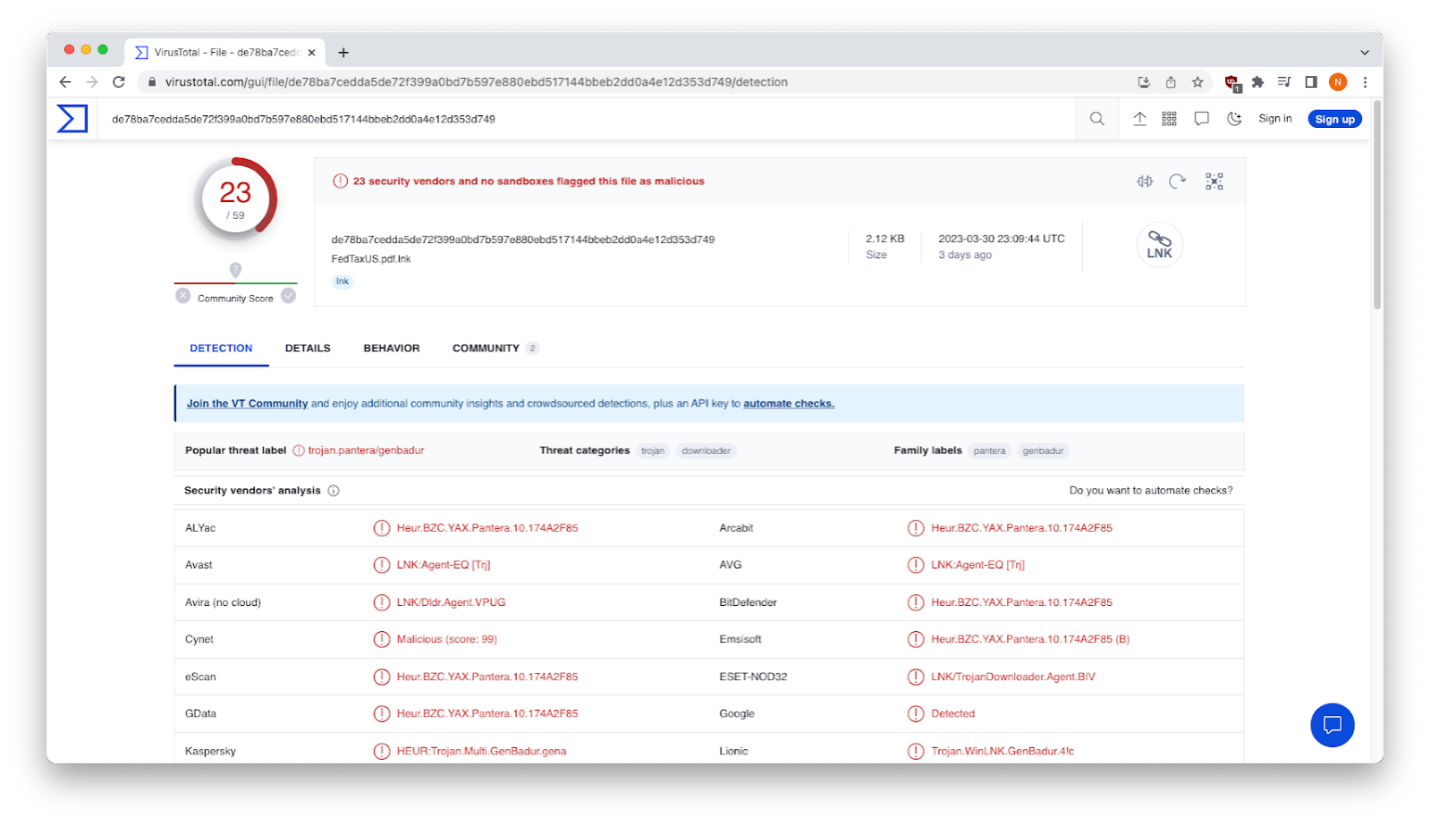
Infected machines give attackers the ability to:
Surveil user behavior with keystroke monitoring, screenshot captures, webcam recordings, and other spyware.
- Deleting, downloading, manipulating, and stealing files.
- Gaining admin privileges and disabling user account control (UAC)
- Installing malware, ransomware, and other viruses.
Recap of Phishing Techniques
- Cloud service abuse - leveraging a legitimate cloud storage service to host malicious files.
- Exploitation of current events - capitalizing on the urgency related to Tax Day.
- Remote access trojan - an attacker uses it to remotely control a victim’s computer.
Best Practices: Guidance and Recommendations
- Don’t open email attachments or links from unknown senders.
- Be careful when viewing or downloading files stored on cloud hosting services. Anyone can use these services to upload malicious files.
- Encrypt all sensitive files and use strong passwords.
Cybercriminals are becoming more sophisticated in their techniques all the time. What’s just as alarming is that services like Mega – founded by criminals like Kim Dotcom – are helping new hackers join the ranks and enabling all phishers to do additional harm. If you're concerned about how a phishing attack could affect your clients or your business, it’s time to take the next step in phishing prevention by calling INKY. Find out what INKY can do for you. Request a free demonstration.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.


