8/3/22
Back in the mists of time, before the turn of the century, wise Internet architects devised a means to redirect a web surfer from one URL to another. This redirection service was enshrined in both browsers and websites so that someone clicking on a link could pass through a first destination on their way to a second.
Looking at it from today’s perspective, with security much closer to top of mind, you might ask, why in the heck would anybody do that? Doesn’t that create an obvious vulnerability? And there is a practical answer, actually a number of answers.
For example, the ability to redirect allows websites to send surfers from an old URL to a new one as the site transitions its domain. A large website like Amazon can buy up adjacent domains (e.g., Amazn.com, Amazonn.com) and have them send surfers to the company’s main page. And there are other reasons, but the most important one — and the one that keeps this architectural element in common use, despite its security implications — is advertising.
Money makes the world go round, and advertising is the lifeblood of Web 2.0. By agreement, an advertiser can take a surfer who intended to go to a certain webpage and drop them on the advertiser’s site first before returning them to their original destination. Given the value of this feature, redirection infrastructure isn’t going away anytime soon.
Within redirection is the concept of the “open redirect,” wherein a site basically lets any random user specify a redirect URL at will and the site allows the transfer of traffic. Open redirect was at the heart of a slew of recent phishing attacks detected by INKY. In these instances, reputable (but unprotected) sites — specifically, American Express and Snapchat — were abused to send traffic to credential harvesting sites.
Quick Take: Attack Flow Overview
- Type: Phishing
- Vector: messages from hijacked accounts or newly created domains with open redirect links to malicious sites
- Payload: Credential harvesting
- Techniques: Brand impersonation, open redirect
- Platform: Google Workspace and Microsoft 365
- Target: Google Workspace and Microsoft 365 users
The Attack
From mid-May through late July, INKY detected many instances of bad actors sending phishing emails that took advantage of open redirect vulnerabilities affecting American Express and Snapchat domains.
Open redirect, a security vulnerability that occurs when a website fails to validate user input, allows bad actors to manipulate the URLs of high reputation domains to redirect victims to malicious sites. Since the first domain name in the manipulated link is in fact the original site’s, the link may appear safe to the casual observer. The trusted domain (e.g., American Express, Snapchat) acts as a temporary landing page before the surfer is redirected to a malicious site.
The following example shows an open redirect link. A surfer sees the link going to a safe site (safe.com) but may not realize this domain will redirect them to a malicious site (malicious.com), which may harvest credentials or distribute malware.
http://safe.com/redirect?url=http://malicious.com
Perhaps websites don’t give open redirect vulnerabilities the attention they deserve because they don’t allow attackers to harm or steal data from the site. From the website operator’s perspective, the only damage that potentially occurs is harm to the site’s reputation. The victims, however, may lose credentials, data, and possibly money.
In both the Snapchat and the American Express exploits, the black hats inserted personally identifiable information (PII) into the URL so that the malicious landing pages could be customized on the fly for the individual victims. And in both, this insertion was disguised by converting it to Base 64 to make it look like a bunch of random characters. We inserted our own random characters into these strings so that the casual observer would not be able to reverse engineer the PII strings.
This vulnerability is well known and enumerated in Mitre’s Common Weakness Enumeration as CWE-601: URL Redirection to Untrusted Site ('Open Redirect'). We reached out to both American Express and Snapchat for reactions.
Snapchat
During a two-and-a-half-month period, INKY engineers detected the snapchat[.]com open redirect vulnerability in 6,812 phishing emails originating from various hijacked accounts.
https://click.snapchat[.]com/aVHG?=http://29781.google.com&af_web_dp=http://qx.oyhob.acrssd[.]org. #.aHR0cHME6Ly9zdG9yYWdlYXBpLmZsZWVrLmNvLzI0MjY4ZTMyLT E2MEmQtNDUxYi1hNTc4LWZhNzg0OTdiZjM4NC1idWWNrZXQvb2Z maWNlMzY1Lmh0bWwjYWNvb3BlckBjcHRsaGVhbHRoLmNvbQ==
Snapchat link manipulated to redirect to malicious site
Phishing emails in the Snapchat open redirect group impersonated DocuSign, FedEx, and Microsoft. All had snapchat open redirects that led to Microsoft credential harvesting sites. In the example above, the redirect had two hops. If the recipient recognized the link as a redirect, they might be fooled into thinking they were going to Google’s benign domain (google.com) rather than the end destination, the malicious site acrssd[.]org.
Open Bug Bounty reported the Snapchat vulnerability to the company on Aug. 4, 2021. However, it remains unpatched.
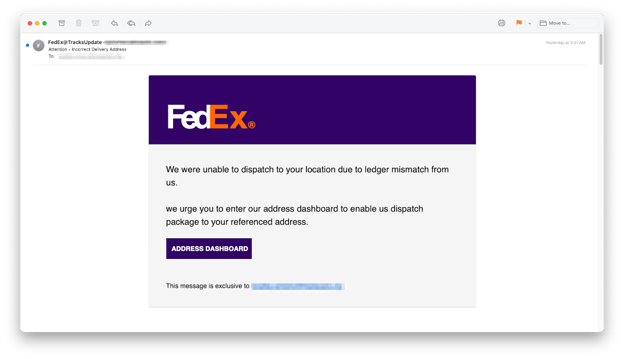
FedEx impersonation email
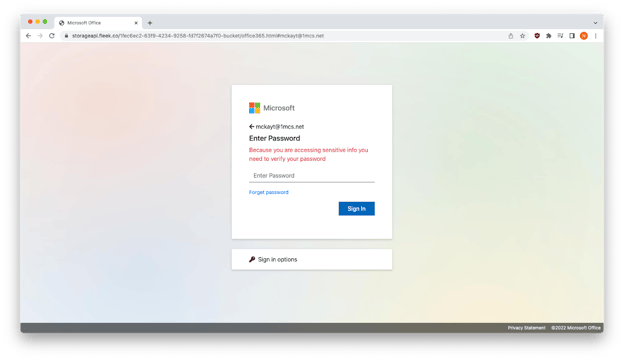
Snapchat open redirect link goes to Microsoft credential harvesting site
American Express
Over a mere two days in late July, INKY engineers detected the americanexpress[.]com open redirect vulnerability in 2,029 phishing emails that originated from newly created domains.
https://www.americanexpress[.]com/Tracking?mid=ALE220718AEMLCATENUS120620PM3736&msrc=ALERTS-NOTIF-PLAT&url=http://58a.upwebseo[.]com/ms/aXJAbXdzbM2xhcmVVuZXJneS5jb20=
American Express link manipulated to redirect to a malicious site
When this phishing campaign first started, the American Express open redirect link went to Microsoft credential harvesting sites, but soon after that, American Express patched the vulnerability. Now, users who click the link end up on a real American Express error page.
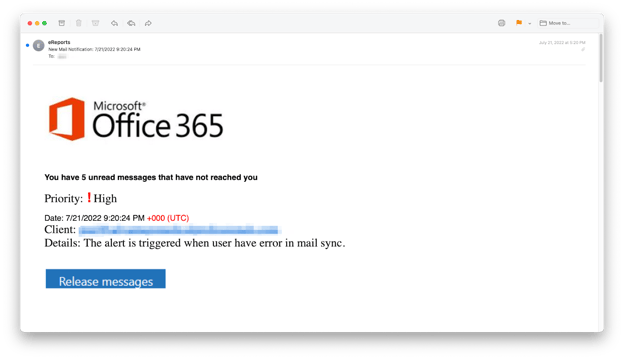
Microsoft impersonation email
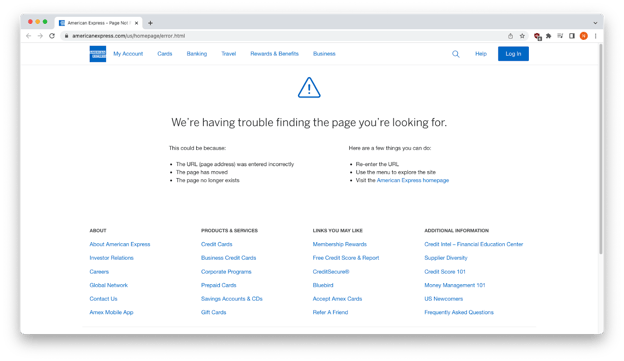
Real American Express error page
Recap of Techniques
-
Brand impersonation — uses brand logos and trademarks to impersonate well-known brands.
-
Credential harvesting — occurs when a victim thinks they are logging in to one of their resource sites but is instead entering credentials into a dialogue box owned by the attackers.
-
Hijacked accounts — are used by phishers to make their emails appear to come from legitimate senders
-
Open redirect links — use trusted domains to redirect victims to malicious sites.
Best Practices: Guidance and Recommendations
When examining links, surfers should keep an eye out for URLs that include, for example, “url=”, “redirect=”, “external-link”, or “proxy”. These strings might indicate that a trusted domain could redirect to another site.
Recipients of emails with links should also examine them for multiple occurrences of “http” in the URL, another potential indication of redirection.
Domain owners can prevent this abuse by avoiding the implementation of redirection in the site architecture.
If the redirection is necessary for commercial reasons, then implementing an allowlist of approved safe links prevents bad actors from inputting malicious links.
Domain owners can also present users with an external redirection disclaimer that requires user clicks before redirecting to external sites.
Ready to see INKY in action? Start a free trial or schedule a demo today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions. Like a security coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Learn more about INKY™ or request an online demonstration today.


