Trends in Phishing Emails Hitting Businesses Today
In law enforcement circles, sophisticated email phishing schemes are known as "business email compromise." More commonly called CEO Fraud or CFO fraud, they are targeting C-suites executives with increasing effectiveness.
Hackers are phishing top company executives, impersonating them, and tricking accounting and business office team members into sending payments to fraudulent accounts. The bad guys either spoof email addresses or use social engineering to gain access to the CEO’s email account. Then, they use that account to request a money transfer. Often, the email includes personal information about the target making it look legitimate.
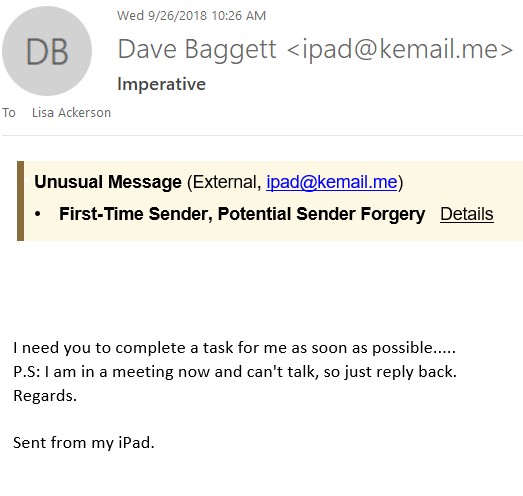 In the CEO fraud example above, the criminals are looking to build a rapport with the employee before they request money or direct the employee to some other type of activity. They have cleverly created a legitimate looking email address that may not necessarily be noticed as fraudulent by the employee. In this above case, Inky knew this wasn’t a ‘usual’ or ‘approved’ email address used by the CEO and flagged it accordingly in the warning banner.
In the CEO fraud example above, the criminals are looking to build a rapport with the employee before they request money or direct the employee to some other type of activity. They have cleverly created a legitimate looking email address that may not necessarily be noticed as fraudulent by the employee. In this above case, Inky knew this wasn’t a ‘usual’ or ‘approved’ email address used by the CEO and flagged it accordingly in the warning banner.
In variations of the CEO fraud scheme, crooks may impersonate attorneys and demand urgent transfers for legal matters by sending a legitimate looking invoice. This scam has been particularly effective when criminals learn of a pending legal action, lawsuit, or acquisition that is in progress. Scammers also will send legal notices, requests to appear in court, or subpoena requests to employees, which include a call to action to avoid further legal problems.
A recent joint task force involving the FBI, Department of Treasury, Department of Homeland Security, the US Postal Service was able to recover $14 million in fraudulent wire transfers. In addition, the six-month investigation netted 72 arrests and seized $2.4 million in cash. Still, this represents just a small portion of what victims have lost. In the last 5 years, there have been more than 78,000 incidents reported, according to the FBI, accounting for more than $12.5 billion in losses. Many other cases go unreported.
Cybercriminals are also targeting senior executives by using spear phishing emails to gain credentials to payroll systems. Once they get access, they can change routing information to redirect employee’s direct deposit to an off-shore account or prepaid card.
Similarly, an email might appear to come from the company CFO to someone in the payroll office asking for them to authorize payment to a new vendor. It might come with an invoice. Opening the invoice looks legitimate, but it also might launch malware for future attacks.
MacEwan University in Edmonton, Alberta, Canada was hit for $9.5 million when fraudulent emails convinced accounting staff members to “update” electronic bank information for vendors, which rerouting legitimate payments to scam accounts.
CEO Fraud or CFO Fraud attacks can compromise the account of senior executives. Not only can this cost money, it can also use the access to uncover proprietary information and damage a company’s reputation. In other cases, they may use the information in brand forgery schemes to mimic company names, logos, and emails to lend credibility to other scams.
Why Most Phishing Email Solutions Fail
A personal note from the CEO asking you to act on their behalf carries weight. A message that your account has been compromised and you need to act right now causes people to act before thinking. Click here, the message might say, to verify your account.
Most phishing email solutions fail because they either fail to recognize the dangers in the email itself, or don’t block malicious emails form getting through to recipients.
There is a Better Solution: Anti-Phishing Solution by Inky
Inky provides complete protection using a comprehensive email phishing and malware detection protocol to keep you safe. Using a sophisticated combination of artificial intelligence, machine learning, and “computer vision,” Inky® Phish Fence can block attacks that other systems fail to detect.
Both incoming and outgoing emails are scanned. Phishing emails are detected and flagged.
Inky® Phish Fence views the email as the end user would. It can detect whether the email is a forgery or phishing email better than human recipients can. Once detected, it can quarantine the email or deliver it with a user-friendly warning while disabling malicious links.
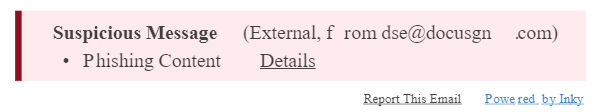
One big advantage of Inky® Phish Fence is that warnings are reported in the email banner as plain text. This allows warning messages to also appear on mobile devices since it is included in the email itself and not in the header. Further, this means that users can make informed decisions about email across any device and report phishing email easily.
Admins are provided with a comprehensive dashboard that provides detailed visibility. You can drill down to individual messages or search date ranges, target users, or specific threat types.
Inky can be installed in just a few hours and works with any email system, including Microsoft Office 365, Exchange and Google Suite.
Schedule a live, personal demo from Inky and see how Inky® Phish Fence can protect you today.



