What a wake-up call for the Oil & Gas industry the Colonial Pipeline hack has turned out to be! Bloomberg is reporting that Colonial has already paid a $5 million ransom to get its digital assets back.
For years, people in the industry have been fretting about aging infrastructure, operations running on old embedded systems that haven’t been updated in years, and the wide variety of equipment that has been jerry-rigged to interact. But nobody did much about it. Now, foreign hackers have shown just how much real-world damage they can wreak on critical but vulnerable U.S. infrastructure, not to mention the financial hit Colonial and all its partners are taking as a result of this clever ransomware attack.
It’s not too reassuring that as of May 12th — as Colonial still projects two weeks before it reaches full operational capability — the company was advertising for a Cyber Security Manager. I hope whoever gets that job is well compensated because the task is going to be like Beaker on the Muppet Show undergoing Dr. Bunsen Honeydew’s twisted experiment. The horse has already fled the barn. With clanky operational systems of the type found far too often in the oil & gas industry, Colonial is no better off now than before the hack.
The attack is so fresh that only Colonial and FBI know for sure, but it’s highly probable that it was started with a phishing email. The hackers were remote (based in Eastern Europe, according to various reports), and there’s just no other way in. Email is the universal communications system that ties together the whole industry. And with the ability to hijack a legitimate account, hackers can send an email that comes from not only a legitimate domain but one known to the recipient.
Similar attacks were perpetrated multiple times on one of the largest automobile manufacturers in the world. In those cases, a secure email gateway (SEG) was in place, but a phishing email got through anyway, and from that compromised machine, hackers were able to infiltrate every machine on the network, and then all at once execute a ransomware operation that encrypted every hard drive in the place with a key that the hackers said they would exchange for money.
Phishing emails that lead to ransomware attacks are usually delivered via malicious macros in documents and spreadsheets. The macro-enabled files are either attached to a phishing email or encountered when the recipient clicks on a malicious link that automatically downloads a file with a nasty payload. If the target interacts with the file, it installs a remote desktop tool (backdoor to gain network access), or it uses a loader that downloads ransomware from an external source.
The Solution to Ransomware Attacks
The best solution is to stop them before they occur, and that involves preventing the successful phishing exploits that set off the whole sorry chain of events. To do that, oil & gas companies need INKY to identify the phish and keep them from landing.
Because of a technique that phishers use, which avoids putting anything bad in the email body and doesn’t involve any malware attachments, INKY engineers had to create a new warning banner (Phishing Site) specifically to flag these ransomware attacks. The poison links are typically on an abused but legitimate website (often a free site where anyone can make a page), and the emails tend to come from legitimate but hijacked email accounts.
These ruses are hard to detect, but the following paragraphs lay out myriad examples of this type of phish that INKY caught. And because INKY sits between the SEG and the recipient’s inbox, every one of these examples is proof that the phish got through the SEG. The hackers used dynamic algorithms to create emails that impersonated the recipient’s domain in the email body to make them appear as if they came from the recipient’s employer.
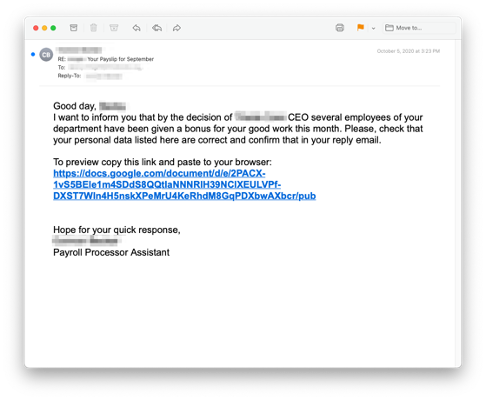
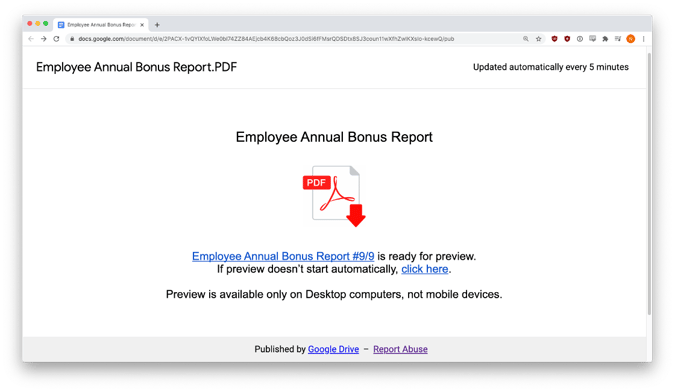
Annual Bonus
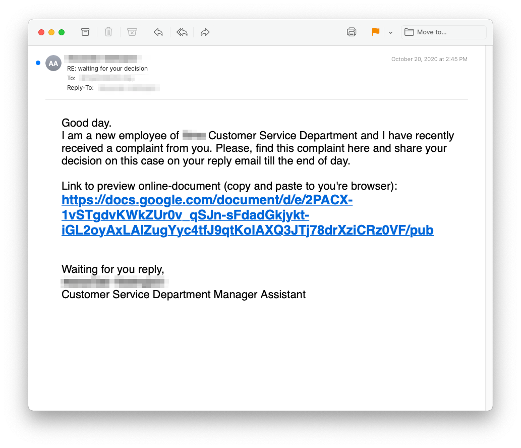
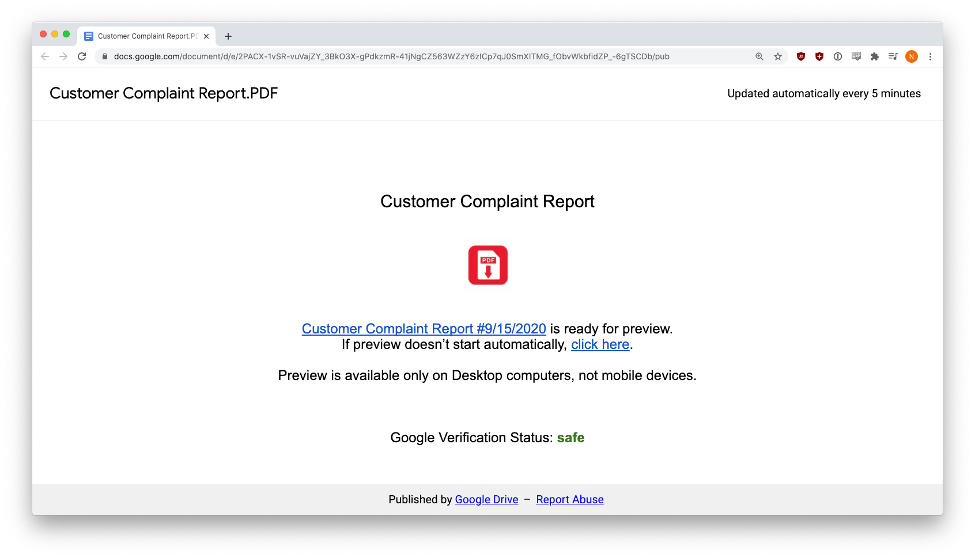
Customer Complaints
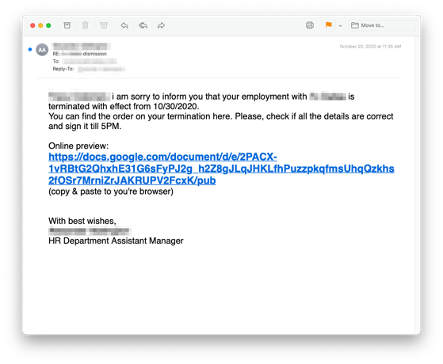
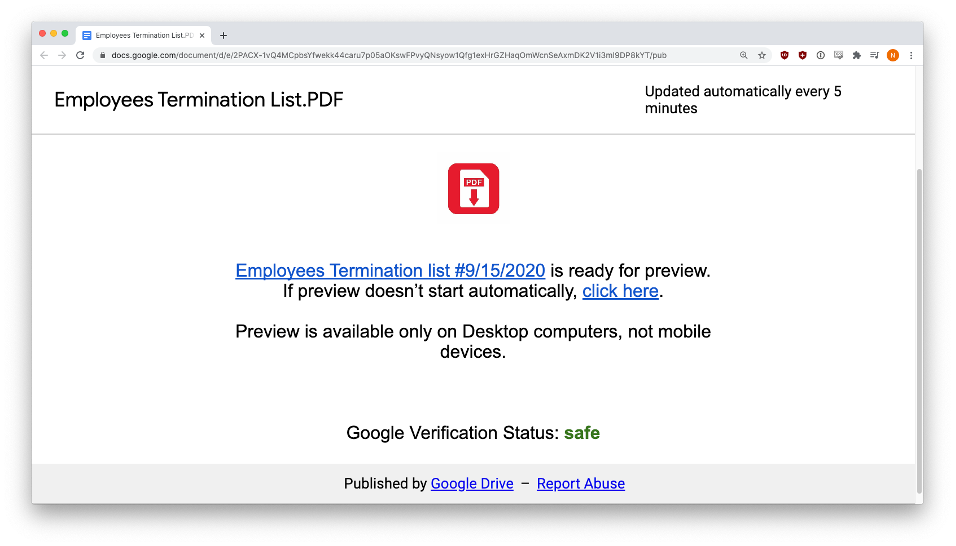
Employee Termination
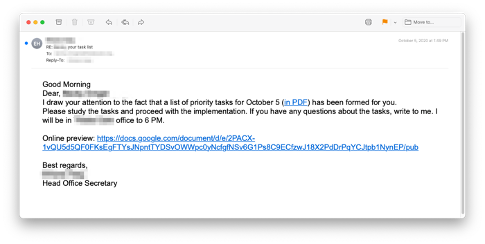
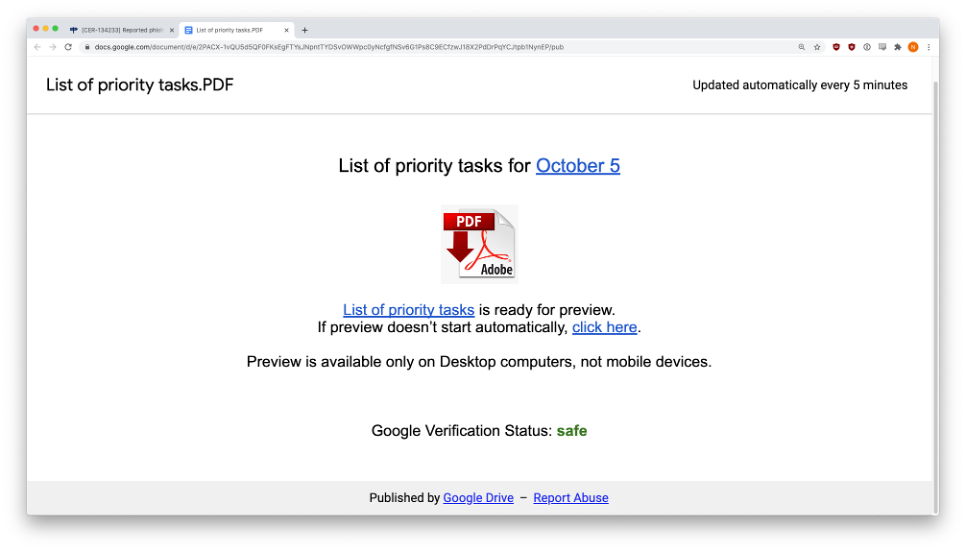
Priority Tasks
Get protected today. Request a free demonstration of INKY to see how we're protecting oil and gas companies from these types of attacks.
----------------------
INKY® is the emerging hero in the war against phishing. An award-winning cloud-based email security solution, INKY® prevents the most complex phishing threats from disrupting or even immobilizing your company’s day-to-day business operations. Using computer vision, artificial intelligence, and machine learning, INKY® is the smartest investment you can make in the security of your organization. INKY® is a proud winner of the NYCx Cybersecurity Moonshot Challenge and finalist in the 2020 RSAC Innovation Sandbox Competition. Learn more about INKY® or request an online demonstration today.


