The emails ask employees to download a “ransomware update” that is actually malware.
Cyberattackers are now using the notoriety of the Colonial Pipeline ransomware attack to leverage further phishing attacks, according to the findings of a cybersecurity company.
It is common for attackers to use widely-covered news events to get people to click on malicious emails and links, and cybersecurity firm INKY said it recently received multiple helpdesk emails about curious emails their customers were receiving.
INKY customers reported receiving emails that discuss the ransomware attack on Colonial Pipeline and ask them to download "ransomware system updates" in order to protect their organization from a similar fate.
The malicious links take users to websites with convincing names — ms-sysupdate.com and selectivepatch.com — both of which are newly created and registered with NameCheap. The same domain that sent the emails also controlled the links, INKY explained in a blog post.
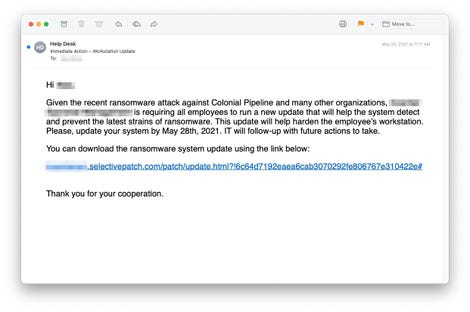
The people behind the attack were able to make the fake websites look even more convincing by designing them with the logo and images from the target company. A download button on the page downloads a "Cobalt Strike" file onto the user's computer called "Ransomware_Update.exe."
Read full article: https://www.zdnet.com/article/hackers-use-colonial-pipeline-ransomware-news-for-phishing-attack/


