In mid-August, the U.S. Senate passed a $1 trillion infrastructure bill, and, capitalizing on the news, phishers set to work right away on a fresh lure. Between Aug. 16-18, INKY detected 41 phishing emails attempting to impersonate the U.S. Department of Transportation (USDOT). The basic pitch was, with a trillion dollars of government money flowing through the system, you, dear target, are being invited to bid for some of this bounty. Most companies aren't infrastructure contractors. So, many of these forays came up dry. But some companies are, and in one of them, a recipient might find such an appeal plausible and enticing.
As they do, the bad guys deployed tried-and-true techniques, but in a novel mix, representing a new pattern. By creating a new domain, exploiting current events, impersonating a known brand, and launching a credential harvesting operation, the phishers came up with an attack just different enough from known strikes to evade standard detection methods.
Although the secure email gateways (SEGs) let their messages through, INKY flagged them as what they are: phish.
Quick Takes: Attack Flow Overview
- Type: phishing
- Vector: newly created domains
- Payload: malicious link
- Techniques: Brand Impersonation
- Platform: Microsoft 365
- Target: Microsoft users
The Attack
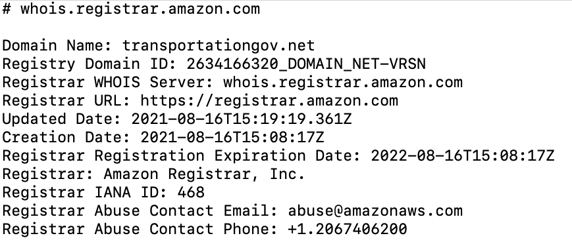
The black hats launched all their phishing emails from the newly created domain (transportationgov[.]net). While this word salad makes no real sense, and government emails most often have a .gov rather than a .net suffix, to someone reading through quickly, the domain name might seem at least somewhere in the ballpark of reality.
Amazon was the new domain’s registrar, and the WHOIS revealed that the name was registered Aug. 16, just before the attack was launched. Essentially, this domain was set up explicitly for this particular exploit.
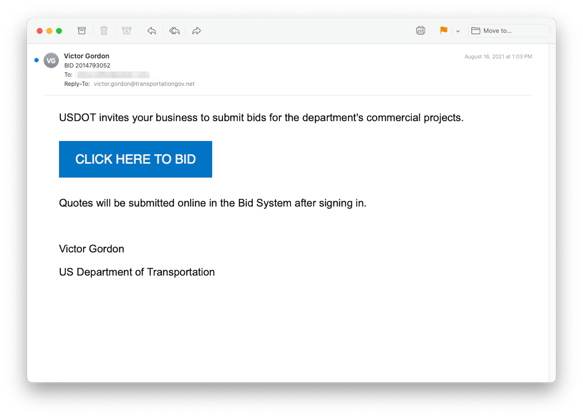
In the initial pitch, recipients were told that USDOT was inviting them to submit a bid for a department project by clicking a big blue button that said, “CLICK HERE TO BID.”
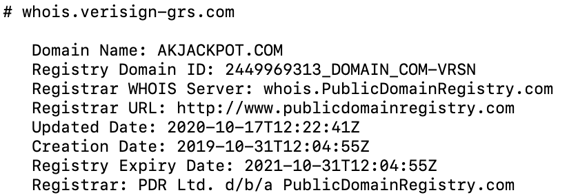
Recipients who clicked on the button were led to a site — transportation.gov.bidprocure.secure.akjackpot[.]com — with reassuring-sounding subdomains like "transportation," “gov," and "secure. But the base domain — akjackpot[.]com — was registered in 2019 and hosts what may or may not be an online casino that appears to cater to Malaysians. Either the site was hijacked, or the site owners are themselves the phishers who used it to impersonate the USDOT.
Once on akjackpot[.]com, the victim was instructed to “Click on the BID button and sign in with your email provider to connect to the network.”
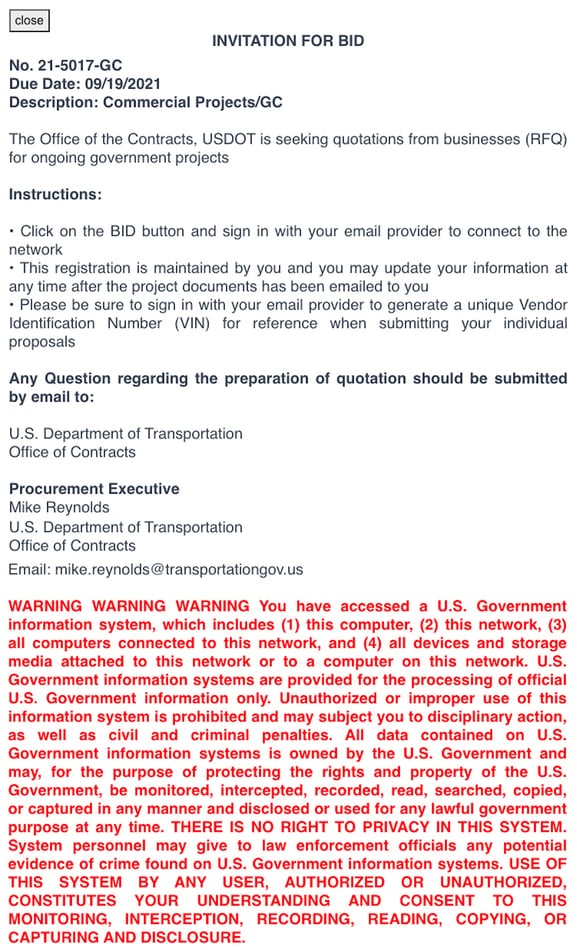
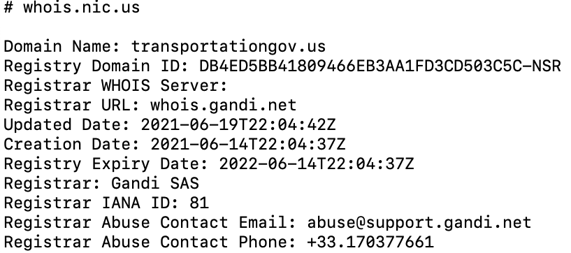
Targets were told to contact “mike.reynolds@transportationgov[.]us” if there were any questions. However, transportationgov[.]us was another newly created domain registered by the phishers.
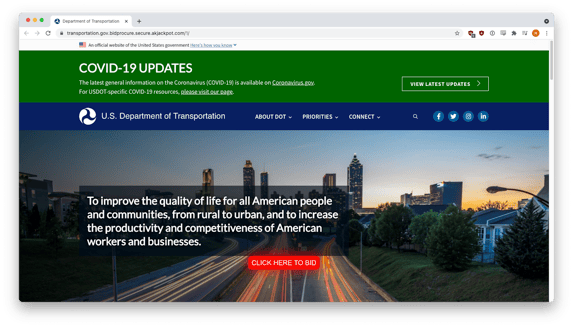
When the victim closed the instructions, an identical copy of the real website for USDOT was revealed. The phishers simply copied HTML and CSS from the real site and pasted it into the phishing site.
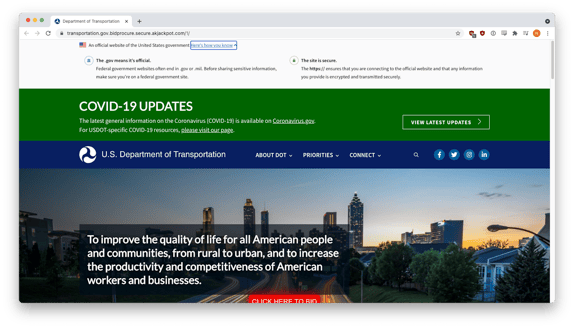
In what may be an ironic twist, the phishers also copied and pasted in a real warning about how to verify actual U.S. government sites. The victim might have noticed that something was up if they had realized that the phishing site domain ended in .com rather than .gov or .mil.
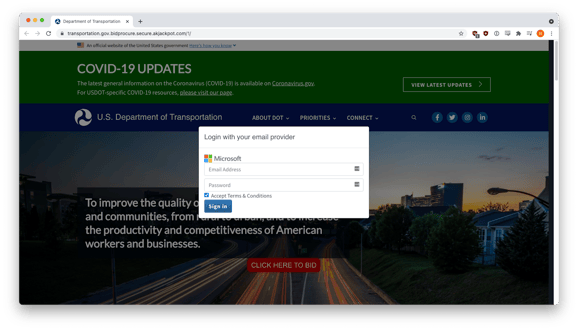
If the target got that far, they were presented with a red “CLICK HERE TO BID” button, which, if clicked, brought up a credential harvesting form with a Microsoft logo. The victim was instructed to “Login with your email provider.”
 When the victim made the first attempt to enter credentials, they were presented with a ReCAPTCHA challenge. On the back end, login credentials had already been harvested and sent to phishers.
When the victim made the first attempt to enter credentials, they were presented with a ReCAPTCHA challenge. On the back end, login credentials had already been harvested and sent to phishers.
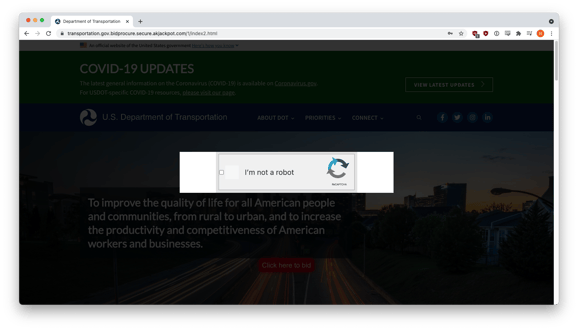
Upon making a second attempt, the victim was presented with a fake error message.
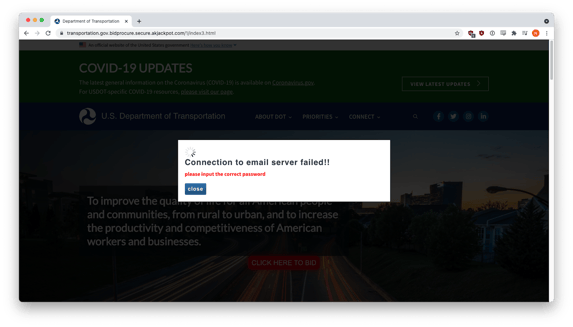
After that, they were redirected to the real USDOT site.
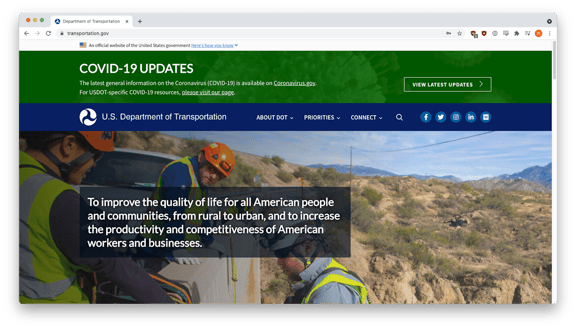
This last move, dumping victims on a real site is an elegant but perhaps unnecessary flourish that phishers often execute as the final step of their sequence. In the con business, this moment is called the “blow-off" and refers to the time after which the perpetrator has obtained what they were after, but before the mark realizes that they've been duped. In the physical world of swindling, the blow-off gives the perpetrator time to getaway. This remnant of older con games sometimes turns up as an artefact in the digital world, where the perpetrators were never “there" in the first place.
Techniques
The phishers used newly created domains because they were able to pass standard email authentication (SPF, DKIM, and DMARC). Since they were brand new, the domains represented zero-day vulnerabilities; they had never been seen before and did not appear in threat intelligence feeds commonly referenced by legacy anti-phishing tools. Without a blemish, these sites did not look malicious.
Several email security vendors use computer vision to detect impersonation sites, but simplistic computer vision would not help in this case because the first thing the victim saw was the instructions, which concealed the actual impersonation site.
Recap of Techniques:
- The exploitation of current events — capitalizes on the recent pass infrastructure bill
- Brand impersonation — spoofs the real USDOT site by directly copying and pasting HTML and CSS from it
- Credential harvesting — occurs when a victim tries to log into what they think is the real USDOT site but actually ends up entering credentials into a form controlled by the phishers
- Newly created domains — are used by phishers to pass most security software tests, allowing phishing emails to slip past corporate defences and into hapless recipients’ inboxes
Best Practices: Guidance and Recommendations
Best practices in the anti-phishing world involve a “belt-and-suspenders" approach. Defences must be multi-layered to catch all the many ways phishers try to penetrate an organization. Standard email security tools are necessary, but not sufficient. Speciality software — which makes use of computer vision, artificial intelligence, deep header and body analysis, and other techniques — is often able to detect zero-day phishing attempts.
In addition, organizations should educate their employees on what to look for. A few examples from the USDOT case include
- an awareness that official U.S. government domains usually end in .gov or .mil rather than .com or another suffix,
- the knowledge that the U.S. government does not typically send out cold emails to solicit bids for projects,
- an understanding that it makes no sense to be asked to log in with email credentials to view a document on a completely different network, and
- an appreciation that new domains are inherently suspicious.
On that last bullet, it doesn’t take much skill or knowledge to do a WHOIS lookup on a site if something seems off.
Fresh Phish examples were discovered and analyzed initially by Bukar Alibe, Data Analyst, INKY
Look for the next edition of INKY’s Fresh Phish blog coming soon.
About INKY
Headquartered in College Park, Maryland, INKY leads the industry in mail protection powered by unique computer vision, artificial intelligence, and machine learning. The company’s flagship product, INKY Phish Fence, uses these novel techniques to “see” each email much like a human does, to block phishing attacks that get through every other system. INKY founder Dave Baggett also co-founded ITA Software, the industry-leading airfare search company purchased by Google in 2011 for $730M, which now powers Google Flights®. For more information, please visit https://INKY.com/.


