Phishers are always trying new things, and they love to bandy about well-known brand names because familiar company logos make people feel comfortable enough to let down their guard. In this particular attack combination, the black hats used both high and low tech to evade anti-phishing radar. The high tech involved newly created and freeware domains, set up to send phishing emails that would not trigger rudimentary email defences (i.e., DMARC analysis of DKIM and SPF records). The low tech was a simple PDF attachment with no poison links or malware in either the attachment or the email itself. These elements were designed expressly to not trigger anti-phishing analysis.
If the victim managed to wend their way to the very end of the process, one of two things (or both!) happened: either the bad guys harvested their banking details and other credentials through an email exchange or over the phone, or the scam runners took the merchandise, never paid for it, and resold it on the black market.
Quick Takes: Attack Flow Overview
- Type: Phishing
- Vector: A fake request for proposal sent from a new or freemail Pfizer look-alike domain
- Payload: PDF attachment to be sent to a different impersonated Pfizer domain
- Techniques: Brand impersonation, free domains, newly created domains
- Platform: Google Workspace (Formerly G Suite) and Microsoft 365 (formerly Office 365)
- Target: Google Workspace and Microsoft 365 users
The Attack
Between Aug. 15 and Dec. 13, INKY detected 410 phishing emails that impersonated pharmaceutical and biotechnology giant Pfizer’s brand in a run of request-for-quotation (RFQ) scams.
The phishing emails themselves originated from a set of confusable domains:
- pfizer-nl[.]com
- pfizer-bv[.]org
- pfizerhtlinc[.]xyz
- pfizertenders[.]xyz
These domains, designed to look like they could be controlled by Pfizer, were all freshly created expressly for the scam and registered with Namecheap, a domain registrar that (helpfully, for the phishers) accepts cryptocurrency as payment.
From the sample that follows, it’s easy to see via WHOIS that pfizer-nl[.]com was created on Dec. 5, a few days before being put to nefarious use.
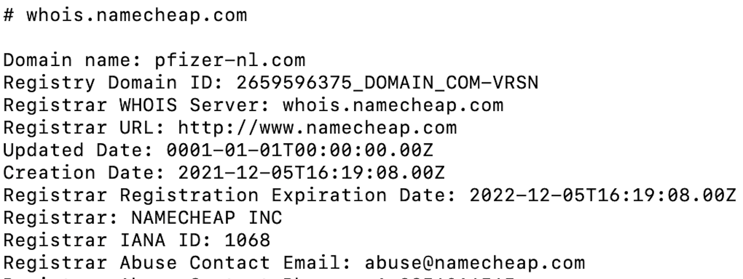
It so happens that Pfizer does have an office in the Netherlands, but the domain is not registered with a .nl suffix, just an ordinary .com one. By analogy, the Pfizer-bv link should relate to a Pfizer office in Bouvet Island, but a cursory examination shows this possibility to be unlikely.
Bouvet Island, 1,500 miles from the Sandwich Islands and 1,000 miles from Antarctica
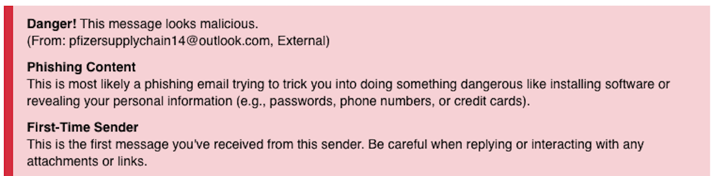
In addition, phishers sent some of the Pfizer-impersonating emails from freemail accounts set up at Gmail, Outlook, and Ziggo. In these cases, the local part of the sender's email address impersonated Pfizer. Despite such attempts at realism, INKY flagged these emails with red for danger.
Here is a sample of subject lines used in the phishing emails:
- Request For Quotation
- Pfizer Request For Quotation
- RFQ
- RFQ URGENT
- RFQ URGENT CARE
- Request for Supply
- Invitation
- Invitation to Bid
Note the element of urgency in some of these subject lines. Urgency is a phisher’s best friend. It causes people to make ill-considered decisions.
Here are two sample emails requesting the recipient to bid. In both cases, the equipment involved had a substantial monetary value.
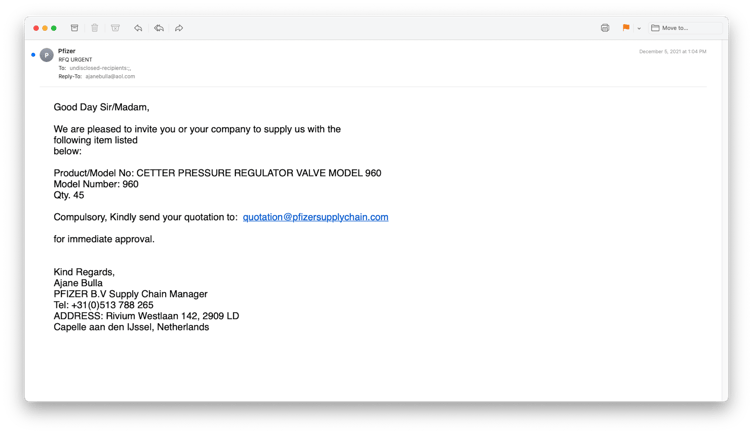
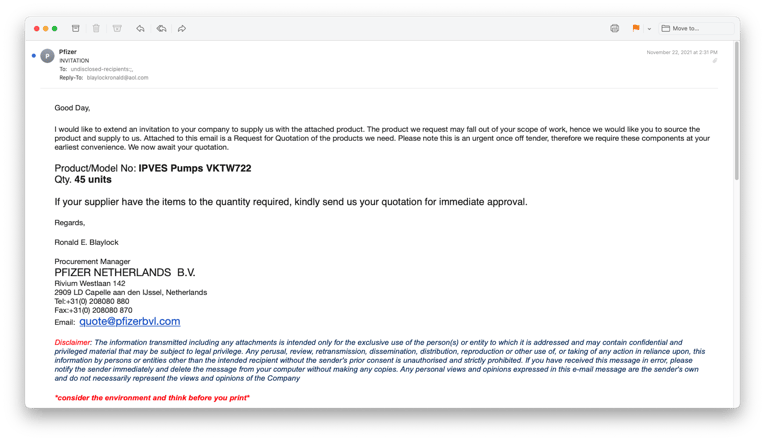
They both claimed that Pzifer was requesting quotes for various industrial engineering supplies, and both had PDF attachments that impersonated Pfizer.
The PDF was three pages long (set out hereunder) and had a few inconsistencies (e.g., different due dates on different pages), but, in general, looked pretty good. The discussion of payment methods and terms set the recipient up for the idea that they would have to share banking details at some point.
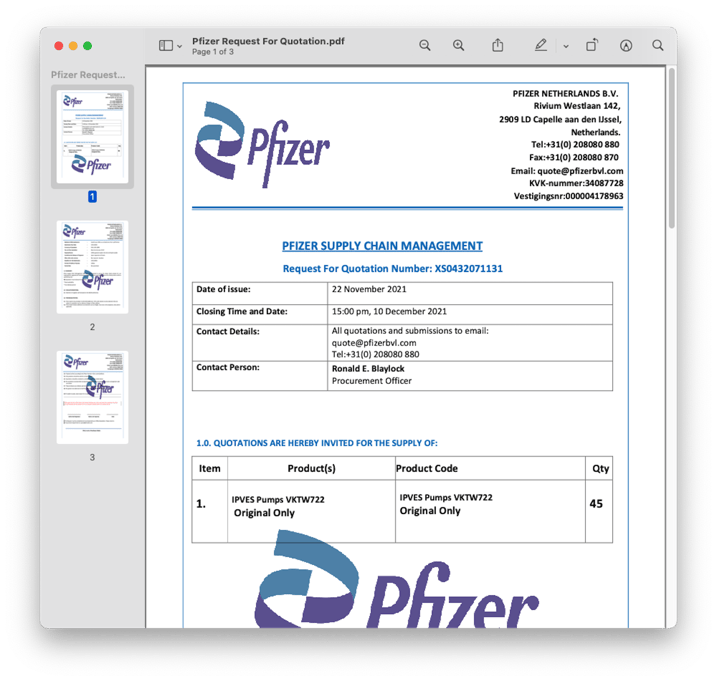

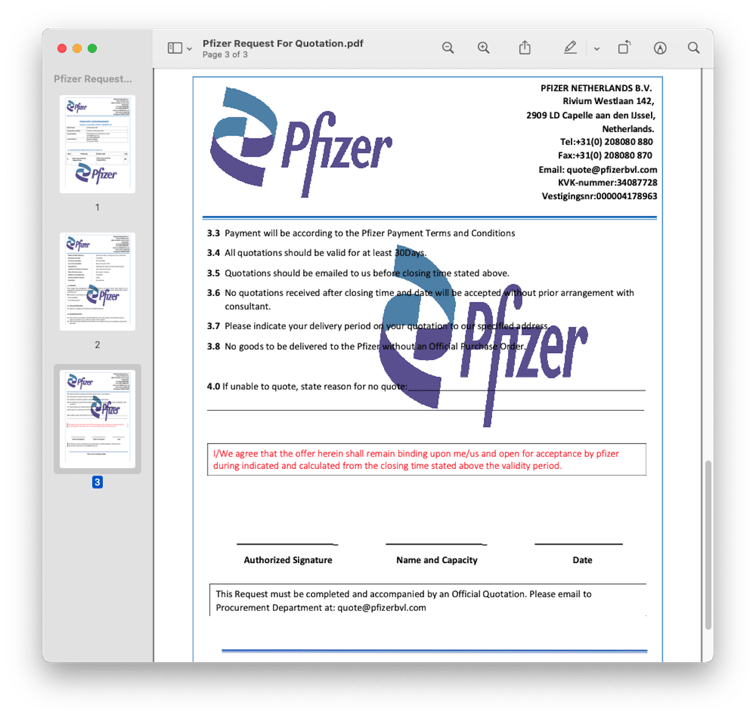 Recipients were instructed to send their quotes to email addresses that impersonated Pfizer (e.g., quote@pfizerbvl[.]com or quotation@pfizersupplychain[.]com).
Recipients were instructed to send their quotes to email addresses that impersonated Pfizer (e.g., quote@pfizerbvl[.]com or quotation@pfizersupplychain[.]com).
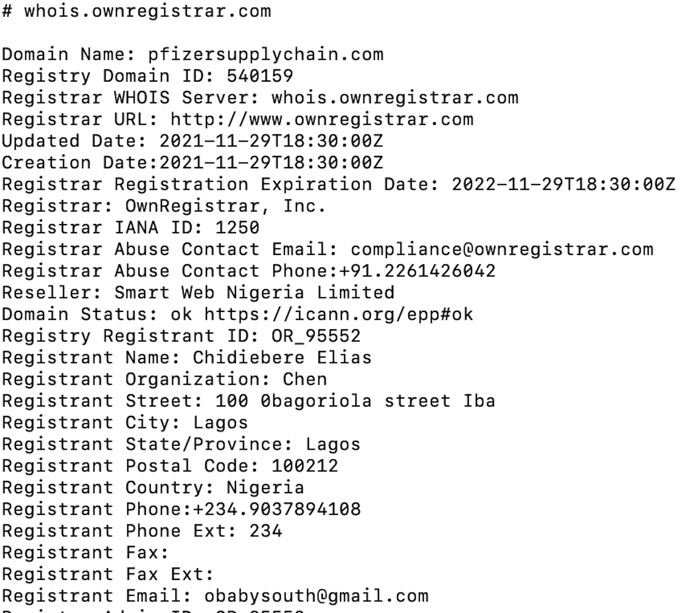
These domains were also newly created with a different domain registrar. The registrant information from a WHOIS lookup for one domain suggested that at least one bad actor was based in Nigeria:
Techniques
The phishers used newly created domains because they were able to pass standard email authentication (SPF, DKIM, and DMARC). Since they were brand new, the domains represented zero-day vulnerabilities; they had never been seen before and did not appear in threat intelligence feeds commonly referenced by legacy anti-phishing tools.
Some of these attacks originated from free-mail services (e.g., Gmail, Hotmail, iCloud), which have high sender reputations. This group was also able to pass email authentication checks.
Finally, there were no malicious attachments or links for email security vendors to scrutinize. Instead, the phishers socially engineered a fake request for proposal PDF attachment and instructed recipients to contact them via look-alike domains that impersonated Pfizer.
Recap of Techniques
- Brand impersonation — a PDF document bearing Pfizer’s logo implies safety and trust
- Abuse of freemail — although freemail accounts do not necessarily have great reputations, they are often clean enough to get past most security measures
- Fresh domains — are not yet known by threat intelligence feeds and therefore pass rudimentary security checks
Best Practices: Guidance and Recommendations
Recipients should be aware that large enterprises like Pfizer do not typically send out cold emails to solicit bids for projects. If a recipient is in a sales department and does business with Pfizer (or, in a similar situation, any other company), they should get in touch with their contact directly by telephone or an initiated email to determine whether the RFQ is legitimate.
It is also highly unlikely that a Pfizer employee would use a freemail account for official business.
The U.S. Department of Transportation, which reports seeing a pickup in exactly this type of scam offers the following guidance:
- Do not click on links or attachments from senders that you do not recognize. Be especially wary of PDF files, and .zip or other compressed or executable file types.
- Do not provide sensitive personal or company information (i.e., usernames and passwords, company financial information, etc.) over email.
Although INKY was unable to follow this scam to its conclusion (since it was designed to minimize a digital trail), we have seen evidence of two possible outcomes:
- The phishers played on the desire of the potential supplier to win the bid and extracted banking and other credentials either via telephone or email exchange, or
- The phishers completed the deal, took delivery of the merchandise, didn’t pay for it, and resold the goods on the black market.
Read more of INKY’s past Fresh Phish, and subscribe to receive our news and articles directly to your inbox.
About INKY
Headquartered in College Park, Maryland, INKY leads the industry in mail protection powered by unique computer vision, artificial intelligence, and machine learning. The company’s flagship product, INKY Phish Fence, uses these novel techniques to “see” each email much like a human does, to block phishing attacks that get through every other system. INKY founder Dave Baggett also co-founded ITA Software, the industry-leading airfare search company purchased by Google in 2011 for $730M, which now powers Google Flights®. For more information, please visit INKY.com/.


