Cyber criminals employ a lot of tricks to get inside your computer network. They may hide a virus inside a file that triggers when you click on it. The virus, once unleashed, can replicate across your systems and do all sorts of damage. They may try to get you to launch a trojan horse program that creates a back door into your computer. They might steal your login credentials and impersonate your company or your employees.
Most companies employ spam filters and regularly scan for viruses, but not as many have adequate anti-phishing software that can stop the method of delivery.
Most security breaches start with phishing email attempts. Malware can be hidden inside an attachment or a link.
If you want to stop malware from infecting your systems, you’ve got to stop phishing attempts.
Shoppers at Target found this out first-hand when a breach exposed credit card data on more than 40 million customers. A phishing email got past the company’s anti-phishing and anti-virus software.
The same thing happened to Anthem when stolen login credentials were compromised by a phishing email sent to employees. It gave cyber criminals access to the company’s network and exposed 80 million records, including health and medical information from the parent company of Blue Cross and Blue Shield.
Phishing emails can steal credentials, launch viruses, and can lock up your data and hold it for ransom. Even the best anti-virus software can’t stop attacks it cannot see coming. It also will not stop new and emerging threats. Almost all anti-virus software relies on a list of known threats. Once a threat is discovered, it can compare new attempts and stop them. However, it will not stop what it does not already know about. Cyber criminals know this. That is why they are constantly evolving their tactics to get past anti-virus software.
Why Phishing Emails Work
Cyber criminals play off your fears and familiarity. It may be FOMO (Fear of Missing Out) on an opportunity to win a new laptop or it may be the fear that your email box is full, and you will miss that important email.
They exploit these fears along with our familiarity with brands to sneak by our defenses. An email that appears to be from UPS or FedEx announcing an update on a delivery seems routine and might not cause suspicions.
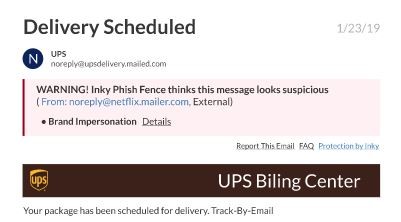
Each of these, however, can launch a virus, trigger ransomware, or send unsuspecting employees to a malicious attachment or spoofed website to steal credentials. The bad guys may also use your email server to launch phishing attack software to attack other organizations using your company’s email.
Once cyber criminals get access to your systems, they can unleash all sorts of attacks which you may not notice happening in time to stop it. According to the Ponemon Institute, the mean time to identify a breach is 191 days and another 66 days to contain the breach. That amounts to giving criminals approximately 8 and a half months of “dwell time” inside your systems before you can remove them.
Virus Software Alone Won’t Stop Phishing Attacks
Two-thirds of viruses and malware start with malicious email attachments. It only takes a single click to launch them. These attacks, delivered by email, can pass through firewalls and anti-virus scans.
As an example, look at what is happening in the healthcare field. A study by the American Medical Association revealed that 83 percent of physicians in the U.S. had experienced a cybersecurity attack. The most common attacks were phishing schemes.
Despite the presence of anti-virus software, nearly 48 percent of those surveyed were exposed to computer viruses. In most cases, the viruses were launched as a result of clicking on email links or email attachments.
You Need Strong Anti-Phishing Software
Phishing software is as important as your anti-virus software. Together, they can help prevent malicious attacks on your computers and computer networks. Anti-virus software alone won’t do the job.
INKY is simply the industry’s best secure email solution. Uniquely effective at recognizing and preventing phishing attacks, INKY uses a combination of machine learning, computer vision, and artificial intelligence to search for signs of fraud other phishing attack software won’t catch.
INKY works on any device
As a cloud-based anti-phishing software solution, it works on Microsoft Exchange, Office 365, G Suite, and nearly every other email software on the market.
By placing strong warning messages directly in the email, it both warns recipients about potential threats and educates them at the same time. Malicious emails are quarantined to prevent users from making a mistake that can be catastrophic.
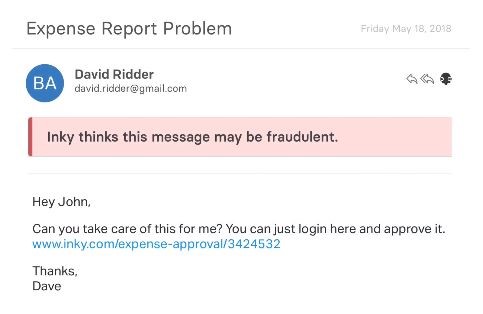
INKY is a secure email protection software that blocks spam, malware, and phishing attacks. It uses domain-specific machine learning and computer vision techniques to identify and block even zero-day phishing emails that pass through other systems.
Check here to see if your organized has been phished.



