Summa Health hospital system has more than 30 locations in northeast Ohio. More than 8,000 employees provide care for more than a million patients every year. Summa Health ranks in the top five percent of hospitals nationwide.
On May 1, 2019, officials noticed unauthorized activity on its email servers. An investigation showed it had been hit by thousands of malicious emails. Four accounts were breached, including two that had gone undiscovered for nearly nine months. While they didn’t find direct evidence that any patient data had been stolen, personally-identifiable medical data for more than 10,000 patients were potentially exposed.
Unfortunately, this story is not uncommon. Every day, more than 156 million phishing emails are sent by cyber criminals. Sixteen million of them make it through filters. About 8 million of them get opened. As many as 80,000 people fall victim, every single day.
Is Your Anti-Phishing Software Doing The Job?
What makes matters worse is that 91% of the breaches at companies analyzed in 2018 thought they were protected by their security software. Even those with e email security software found their defenses less than adequate.
Phishing attack software comes in many variations. Microsoft Office 365, MS Exchange, and Google G Suite have built-in security. A search for anti-phishing software will show millions of results. With so much software on the market and so much news about phishing emails out there, why are cyber criminals so effective?
“Cybercriminals steal hundreds of millions of dollars each year with new impunity,” said Roger Grimes writing in CS Online. “For everyone that gets caught, 10,000 go free – maybe more.”
Phishing Attack Software That Works
If your organization hasn’t been hit by a phishing attack yet, consider yourself lucky. However, you can’t depend on luck to keep your data secure. You need anti-phishing software that provides a strong defense:
- Detects incoming phishing attempts
- Prevents phishing emails from getting through your defenses
- Provides strong, easily identifiable warnings
- Educates users so they can stay vigilant
INKY is the industry’s leading anti-phishing software that detects and prevents phishing attacks. Employing machine learning, artificial intelligence, and computer vision, INKY’s phishing attack software solution stops email phishing attacks that others can’t.
Most software checks email addresses and potentially malicious links against lists of known threat actors. INKY goes further by examining every link and email for signs of forgery. INKY’s proprietary computer vision can spot even the most minute difference in brand logos down to the pixel.
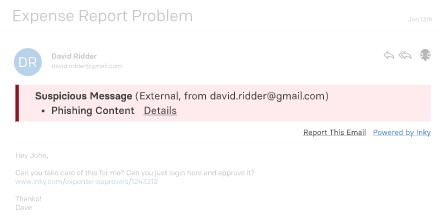
Phishing warning banners embedded directly in the email flag suspicious emails and offer specific guidance. These warnings show up on desktop and mobile devices, unlike some other phishing software that warns by appending the subject line which gets truncated on many mobile devices.
INKY’s machine learning builds social graphs and behavior profiles. When it spots an email that doesn’t match a known profile or suspects suspicious behavior, it sends an impersonation warning.
Stop Email Phishing Attacks
INKY is effective at stopping a variety of email phishing attacks:
- Whaling attacks and CEO fraud
- Spear phishing
- Brand forgeries
- Business email compromise
- Zero Day attacks
- Domain spoofing
- Malware
- Ransomware
Whaling attacks and CEO fraud happen when criminals impersonate C-level executives. They may ask for an urgent wire transfer or access to sensitive information. Spear phishing targets specific individuals by sending emails that appear to come from a trusted source, such as a friend or colleague. Brand forgeries impersonate well-known companies to try and steal login credentials.
Unlike most anti-phishing software, INKY doesn’t just check URLs and email addresses against lists of known threats, it uses computer vision to detect company logos and determine whether the email matches up to legitimate senders.
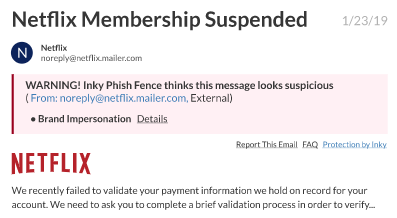
Business email compromise (BEC) accounted for more than $2.7 billion in financial losses in 2018 according to the FBI. Sophisticated email attacks target organizations and suppliers. INKY spots BEC with astonishing accuracy.
Zero-day attacks target known exploits in software that has yet to be patched. These zero-day attacks slip by most phishing attack software solutions, but not INKY.
Domain spoofing impersonates trusted email addresses. They may use a slight variation of the official email or hidden characters that users can easily miss. INKY’s intelligent machine learning algorithms prevent spoofing by finding even minute abnormalities.
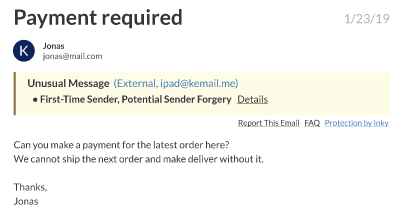
More than two-thirds of Malware and Ransomware start with an infected email link or attachment. INKY checks for suspicious behavior and flags users before they open potentially dangerous links and attachments.
Protect Yourself From Phishing Attacks
More than $1.4 billion is lost by businesses to email fraud every year. You can’t afford to leave yourself unprotected from phishing attacks.
Download our Special Phishing Report to learn how you can better protect yourself your employees, customers, and partner from phishing emails.
Request a demo to see if your company has already been phished.
SOURCES:
- https://smallbiztrends.com/2018/09/phishing-attack-examples.html
- https://resources.infosecinstitute.com/5-real-world-examples-business-email-compromise/#gref
- https://www.trendmicro.com/vinfo/us/security/news/phishing
- https://fraudwatchinternational.com/phishing/phishing-attack-trends-for-2019/
- https://www.infosec.gov.hk/english/anti/recent.html
- https://gizmodo.com/how-phishing-scams-are-evolving-and-how-not-to-get-caug-1832618224
- https://www.infosecurity-magazine.com/news/uk-firms-hit-by-attacks-every-50/
- https://healthitsecurity.com/news/summa-health-alive-hospice-report-data-breaches-from-email-hacks
- https://www.summahealth.org/about-us/about-summa/history
- https://www.cleveland.com/akron/2019/02/summa-health-among-top-five-percent-of-us-hospitals-according-to-healthgrades-health-care-rating-service.html
- https://www.getcybersafe.gc.ca/cnt/rsrcs/nfgrphcs/nfgrphcs-2012-10-11-en.aspx
- https://www.csoonline.com/article/3147398/why-its-so-hard-to-prosecute-cyber-criminals.html
- https://inky.com/
- https://inky.com/phishing-threats/ceo-fraud/
- https://inky.com/phishing-threats/whaling-attacks/
- https://inky.com/phishing-threats/spear-phishing/
- https://inky.com/phishing-threats/brand-forgery/
- https://threatpost.com/fbi-bec-scam-losses-double/144038/
- https://www.fbi.gov/news/stories/ic3-releases-2018-internet-crime-report-042219
- https://inky.com/phishing-threats/domain-spoofing/



